Just as we protect the IT physical infrastructure such as Servers, Storage Systems and network components etc, it is also important for organizations to protect the logical infrastructure such as applications and data. Typically organizations implement data protection solutions in order to protect the data from accidentally deleting files, application crashes, data corruption, and disaster. Organization’s data may be protected at local location and as well as at a remote location to ensure the availability of service. One of the key data protection solutions widely implemented is Backup and the vendors & products who are offering these backup solutions are like EMC Avamar and Netbackup etc.
A backup is an additional copy of production data, created and retained for the purpose of recovering the lost or corrupted data. Organizations need fast backup and recovery of data to meet their service level agreements. Most organizations spend a considerable amount of time and money protecting their application data but give less attention to protecting their server configurations. During disaster recovery, server configurations must also be re-created before the application and data are accessible to the user. The process of system recovery involves reinstalling the operating system, applications, and server settings and then recovering the data. So it is important to backup both application data and server configurations.
One of the major roles of backup and recovery is functioning as part of a business continuity
plan (BCP). In a BCP, backups sit alongside other storage-related technologies such as replication and snapshots. Backups are an important part of disaster recovery and business continuity plans. So organizations has to make sure that backups are reliable and can be easily and reliably recovered. Evaluating backup technologies, recovery, and retention requirements for data and applications is an essential step to ensure successful implementation of a backup and recovery solution.
Backups are performed for three primary purposes – disaster recovery, operational restores, and long-term storage.
- Disaster recovery addresses the requirement to restore all, or a large part of, an IT infrastructure in the event of a major disaster. The backup copies are used for restoring data at an alternate site when the primary site is incapacitated due to a disaster. Based on recovery requirements, organizations use different backup strategies for disaster recovery.
- Operational backup is a backup of data at a point-in-time (PIT) for the purpose of restoring data in the event of data loss or logical corruptions that may occur during routine processing. An example of an operational backup is a backup taken just before a major change to a production system occurs. This ensures the availability of a clean copy of production data if the change corrupts the production data.
- Backups are also performed to address long-term storage requirements. For example, an organization may require to keep transaction records and other business records required for regulatory compliance. These types are also referred as Archives.
Important Considerations for Data Protection (Data Backup) Solution for an Organization
Organizations need reliable and efficient backup and recovery solutions to meet the required service levels. Organizations need to understand some of the key backup and recovery considerations while implementing the solutions. Additionally, as the organization moves towards next generation technologies like Cloud, IOT and Big Data, it is important for the backup applications to integrate with various robust business applications along with next generation applications (social, mobile, analytics, and cloud) to protect the business data.
It is also important to ensure that most of the backup and recovery operations need to be automated. Typically, the backup processes are automated through scheduling to reduce the manual intervention. With the ability to rapidly add VMs, the backup solution needs to automatically provision backup to the new VMs. The solution should recognize when a new VM is created and apply an appropriate protection policy automatically. Similarly, when a VM is removed from the environment, the protection policy should be removed as well.
IT environment has large volume of redundant data. Backing up of redundant data would significantly impact the backup window and increase the operating expenditure. Backup applications should support deduplication techniques to overcome these challenges. Deduplication also provides the extended retention of backup copies. Backup solutions should also support WAN optimization techniques, to reduce the network bandwidth requirement, when taking remote office backup.
When planning a backup solution, it is important to evaluate the restore needs. Most common restores involve application data, e-mail, and specific files, but sometimes the user or business may require complete restore of a VM. To meet the various restore demand, the backup application should support recovery of data at both the file and the VM-level.
Organizations can provide the capability to their consumers for self-service file restores. Particularly, when an organization offers backup services, they may store the consumers backup data on a same backup device. So it is important that the backup device should support secure multi-tenancy. The backup management software should have single management interface to monitor and manage the whole backup infrastructure centrally.
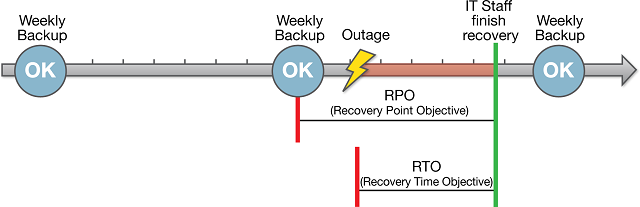
Recovery Point Objective (RPO) & Recovery Time Objective (RTO)
The amount of data loss and downtime that a business or organization can endure in terms of RPO and RTO are the primary considerations in selecting and implementing a specific backup strategy.
A Recovery Point Objective (RPO) is the point in time to which a service can be restored or recovered. So, if you have an RPO of 24 hours, you will be able to recover a service or application to the state it was in no more than 24 hours ago. At any given point in time, you will have a valid backup of the database that is no more than 24 hours old within your stated RPO of 24 hours.
A recovery time objective (RTO) is significantly different from a recovery point objective. Whereas a recovery point objective says that you can recover a system or application to how it was within a certain given time window, a recovery time objective states how long it will take you to restore or recover. For example, it might take you 8 hours to recover a system to the state it was in 24 hours ago. Generally, when defining and deciding RTOs, make sure to factor the below points as well.
- The time it takes to recall tapes from off-site storage.
- The time it takes to rally staff and get logged on and working on the recovery
To meet the defined RPO & RTO, organizations should choose the appropriate backup target, and backup type to minimize the recovery time. For example, a restore from tapes takes longer to complete than a restore from disks. The organization can also implement a strategy where the inactive data can be archived before performing backup. This would reduce backup windows and also reduce backup infrastructure cost.
When it comes to backups, recovery point objectives are a major consideration. If the business requires an RPO of 5 minutes for a certain application, then a daily backup of that system will not meet that RPO, and you will need to use different technologies such as snapshots. Because with traditional tape-based backups, the normal minimum RPO is one day (24 hours), because it’s usually not realistic to make traditional backups to tape more frequently than once per day.
In these situations, if more-granular RPOs are required, traditional backups can be augmented with technologies such as snapshots. These snapshots could be taken, for example, every 15 minutes but kept for only one day. Then each full traditional backup to tape could be taken once per day and kept for 12 months. This configuration will allow for a recovery of the application to any 15-minute point within the last 24 hours.