In today’s rapidly evolving business landscape, cloud computing has become a cornerstone of digital transformation. Oracle Cloud Infrastructure (OCI) stands out as a robust and versatile platform to empower organizations in this journey. However, the success of cloud adoption hinges on a well-architected foundation. This is where Oracle Cloud Landing Zones (OCLZs) come into play, serving as a crucial enabler for a seamless and secure cloud experience.
In this comprehensive guide, we’ll delve into the intricacies of OELZs, with a particular focus on the enhanced capabilities of Oracle Enterprise Landing Zone v2 (OELZ v2). Whether you’re a seasoned cloud architect or a budding cloud engineer, this blog post will equip you with the knowledge and insights needed to architect, deploy, and manage a successful cloud environment on OCI.
Read: What is a cloud Landing zone and why it is important.
We’ll explore the evolution of OELZs, highlighting the key differences between OELZ v1 and the more advanced OELZ v2. You’ll gain a deep understanding of OELZ v2’s modular architecture, its comprehensive security features, and the streamlined user experience it offers. We’ll also provide step-by-step guidance on deploying OELZ v2 using Terraform CLI and Resource Manager, along with best practices for multi-cloud integration and advanced configurations.
1. Oracle Cloud Landing Zones (OCLZs) Introduction
In essence, a Cloud Landing Zone is a pre-provisioned, secure, and scalable environment within a cloud platform that acts as a starting point for your cloud deployments. It establishes a standardized framework with predefined configurations, security controls, and governance mechanisms. Oracle Cloud Landing Zones (OCLZs) take this concept further by providing a structured approach to onboarding workloads onto OCI, ensuring consistency, compliance, and adherence to best practices across your entire cloud estate.
Why are Oracle Cloud Landing Zones Essential?
Investing in a well-designed OCLZ can significantly impact your organization’s cloud journey. Here’s why they are essential:
Read: The complete guide on AWS Landing Zone Architecture
- Accelerated Time-to-Value: OCLZs streamline the onboarding process, enabling you to deploy workloads faster and realize the benefits of your cloud investments sooner. By automating provisioning and configuration tasks, OCLZs eliminate manual effort and reduce the time it takes to set up new environments.
- Enhanced Security and Compliance: OCLZs incorporate industry-leading security best practices, such as network segmentation, encryption, and identity and access management (IAM). These measures safeguard your critical data and applications, ensuring they are protected from unauthorized access and potential threats. Additionally, OCLZs help you meet regulatory compliance requirements, giving you peace of mind regarding data security and privacy.
- Operational Efficiency: OCLZs automate repetitive tasks, minimize manual errors, and enable centralized management of your cloud resources. This frees up your IT teams from mundane operational activities, allowing them to focus on strategic initiatives that drive innovation and business growth.
- Cost Optimization: By implementing resource tagging, budgets, and usage reports, OCLZs provide transparency into your cloud spending. You can easily track and analyze your cloud costs, identify areas for optimization, and make informed decisions to control expenses.
2. Oracle Cloud Landing Zones (OELZ) v1 and OELZ v2: Differences
Oracle Enterprise Landing Zone (OELZ) has evolved significantly from v1 to v2, offering a more robust and adaptable foundation for your cloud deployments on Oracle Cloud Infrastructure (OCI). Here’s a breakdown of the key differences between the two versions.
| Feature | OELZ v1 | OELZ v2 |
|---|---|---|
| Design Philosophy | Monolithic | Modular |
| Security | Basic controls | Enhanced controls, CIS Benchmark Level 1 support |
| Identity Mgmt | Basic IAM integration | Enhanced IAM with OCI Identity Domains |
| Access Control | Role-based access control (RBAC) | Granular RBAC, Attribute-based access control (ABAC) |
| User Experience | Less flexible, steeper learning curve | Simplified deployment, improved user inter |
Design Philosophy: Modular vs. Monolithic
- OELZ v1: Followed a monolithic architecture where all components were tightly integrated. This made it less flexible for customization and scaling.
- OELZ v2: Introduces a modular design. Components like networking, security, and identity are decoupled, allowing you to select and deploy only the modules you need. This modularity enhances scalability, flexibility, and ease of maintenance.
New Features in OELZ v2
- Enhanced Security:
- CIS Benchmark Level 1 Support: OELZ v2 includes out-of-the-box support for CIS benchmarks, ensuring a strong security foundation.
- Security Zones: Provide an additional layer of isolation and protection for sensitive workloads.
- Data Safe: Integrates with Data Safe for comprehensive data discovery, classification, and security assessment.
- Enhanced Identity Management:
- OCI Identity Domains: Replaces the previous Oracle Identity Cloud Service (IDCS) integration. Offers more granular control over identity and access management within your OCI tenancy.
- Federation: Enables seamless integration with external identity providers like Microsoft Active Directory or Okta.
- Enhanced Access Control:
- Attribute-Based Access Control (ABAC): Allows for more fine-grained access control based on attributes like resource tags or user attributes, beyond just roles.
Overall User Experience Improvements
- Simplified Deployment: OELZ v2 leverages Terraform modules for streamlined and automated deployment, making it easier to set up and manage your landing zone.
- Improved User Interface: The OCI console has been enhanced with a dedicated OELZ dashboard, providing better visibility into your landing zone’s configuration and status.
- Comprehensive Documentation: OELZ v2 boasts significantly improved documentation, making it easier for users to understand and implement the framework.
Which Version Should You Choose?
If you are starting fresh, OELZ v2 is the clear winner. Its modular design, enhanced security, improved identity management, and superior user experience make it the ideal choice for building a modern and scalable cloud foundation on OCI.
Read: GenAI basics and fundamentals
However, if you are already using OELZ v1, transitioning to v2 requires careful planning and consideration. Oracle provides migration guidance to help you make the switch.
3. Oracle Enterprise Landing Zone v2 (OELZ v2) Overview:
Oracle Enterprise Landing Zone v2 (OELZ v2) is a modernized framework built on a modular design to easily scale alongside your growing environment. It leverages Terraform modules to simplify the setup of a secure, multi-account infrastructure within Oracle Cloud Infrastructure (OCI).
Key Uses:
- Multi-Cloud Integration: Easily connect OCI with other cloud platforms like Microsoft Azure, establishing a hybrid cloud environment. This allows organizations to leverage the strengths of different cloud providers, optimize costs, and avoid vendor lock-in.
- Robust Governance & Compliance: Leverage pre-configured policies and guardrails to ensure your OCI setup aligns with industry standards like ISO27001 and PCI DSS. OELZ v2 also includes features to help you meet other compliance standards, ensuring that your cloud environment adheres to industry best practices and regulatory requirements.
- Effortless Scaling: Automate the provisioning of new accounts, users, and resources, allowing your OCI infrastructure to expand in line with your organization’s growth. For example, OELZ v2 can automatically create new virtual machines or storage volumes as needed to accommodate increased demand.
Main Goals:
- Minimize the time and effort required for setup and deployment.
- Provide a solid architectural foundation for your OCI environment.
- Offer the flexibility to customize and adapt the implementation to suit your organization’s unique needs.
Key Design Principles
OELZ v2 is designed with the following key principles:
- Modularity: OELZ v2 is built with a modular architecture, enabling you to deploy only the components necessary for your specific use case. This enhances flexibility and simplifies customization, making it easier to scale your environment as your needs grow.
- Hub-and-Spoke Architecture: This architecture enhances security and isolation by separating environments into distinct “spokes” (workloads) connected to a central “hub” (shared services). This promotes better organization and granular control over resources.
- Security First: OELZ v2 prioritizes security by incorporating industry best practices and standards, such as CIS Benchmarks. Features like network segmentation, identity and access management (IAM), and data encryption protect your resources from unauthorized access and potential threats.
- Automation through Infrastructure as Code (IaC): OELZ v2 utilizes Terraform to automate infrastructure provisioning and management. This ensures consistency, reproducibility, and reduces the risk of human error, streamlining your cloud operations and making them more efficient.
Read: Quick guide to Google Cloud Platform Landing Zone
These core principles guide the design and implementation of OELZ v2, making it a robust and flexible framework for building secure and scalable cloud environments on Oracle Cloud Infrastructure (OCI).
4. Oracle Enterprise Landing Zone v2 (OELZ v2) Architecture
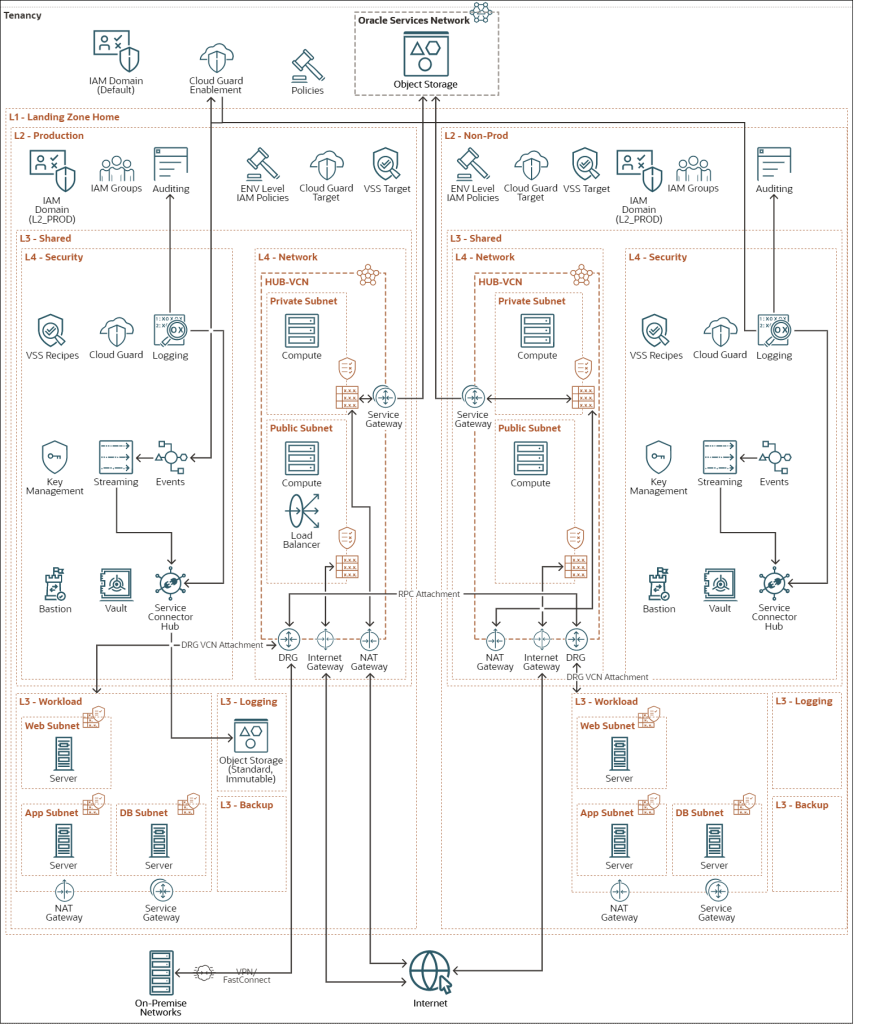
Oracle Enterprise Landing Zone v2 (OELZ v2) is a comprehensive framework designed to streamline and secure your cloud environment on Oracle Cloud Infrastructure (OCI). It offers a modular approach, allowing you to select and deploy only the components you need, making it adaptable to your specific requirements.
The architecture revolves around a hub-and-spoke model, where a central “hub” network houses shared services like identity and access management (IAM), logging, and monitoring. Individual “spokes” represent isolated environments for your workloads, enhancing security and control.
Key Components
OELZ v2 encompasses several key components that work together to provide a secure and scalable cloud foundation:
- Compartments: Logical containers used to organize and isolate your resources, simplifying management and access control.
- Tags: Metadata assigned to resources for efficient organization, filtering, and cost tracking.
- Budgets and Alerts: Tools for setting spending limits and receiving notifications when usage approaches or exceeds those limits.
- Oracle Cloud Infrastructure Identity and Access Management (IAM): A service for controlling access to your cloud resources, ensuring that only authorized users and groups can perform actions.
- Networking and Connectivity: Establishes a virtual cloud network (VCN), subnets, and other networking resources required for your workloads to communicate with each other and the internet.
- Security: Enables a strong security posture by integrating OCI security services like Oracle Cloud Guard (for threat detection), OCI Vulnerability Scanning, and OCI Bastion (for secure administrative access).
a. Network and Connectivity: The Hub-and-Spoke Model
The hub-and-spoke architecture is a fundamental aspect of OELZ v2, offering several advantages:
- Isolation: Each spoke operates as an independent compartment, providing an extra layer of security and isolation for your workloads.
- Scalability: You can easily add or remove spokes to accommodate changing needs or support different teams or projects.
- Simplified Networking: The hub acts as a central point for network traffic, streamlining the overall architecture and enhancing security.
- Efficient Resource Management: Each spoke can be managed independently, allowing for better resource allocation and utilization.
- Cost Optimization: Centralizing resources like VPN gateways and load balancers in the hub can lead to cost savings.
- Effective Governance: The central hub simplifies the application of governance rules and policies across your entire infrastructure, providing a clear view of resources and activities.
b. Monitoring and Logging
OELZ v2 includes robust monitoring and logging capabilities, crucial for maintaining the health, performance, and security of your OCI environment. These tools help you track resource utilization, detect anomalies, and troubleshoot issues.
c. Multi-Environment Support
OELZ v2 supports multiple environments, such as production and non-production, each isolated with separate identity domains, hub-and-spoke networks, Cloud Guard configurations, and logging setups.
d. Identity and Access Management
OELZ v2 leverages OCI Identity and Access Management (IAM) for granular control over who can access your cloud resources and what actions they can perform. It also supports federation with Microsoft Active Directory for seamless integration with existing identity systems.
e. Compliance
OELZ v2 incorporates a set of pre-built policies and guardrails that help you establish a strong security foundation and work towards compliance with industry standards like CIS 1.2 Level 1. These security controls provide a baseline for protecting your data and applications in the cloud.
5. Oracle Enterprise Landing Zone v2 (OELZ v2) Functional Modules
| Module | Primary Function |
|---|---|
| Landing Zone | Orchestrates the entire landing zone creation process. |
| Environment | Aggregates other modules to form a single, isolated environment. |
| Compartments | Creates a structured hierarchy of compartments within an environment. |
| Budget and Tagging | Provides tools for cost management and governance. |
| Identity | Creates and configures an identity domain within an environment. |
| Network | Establishes the network architecture with a hub-and-spoke design. |
| Security | Implements security best practices and services. |
| Monitoring | Enables monitoring of the health and performance of the environment. |
| Logging | Captures and manages log data from various sources. |
| Workload | Simplifies the deployment of resources for new workloads. |
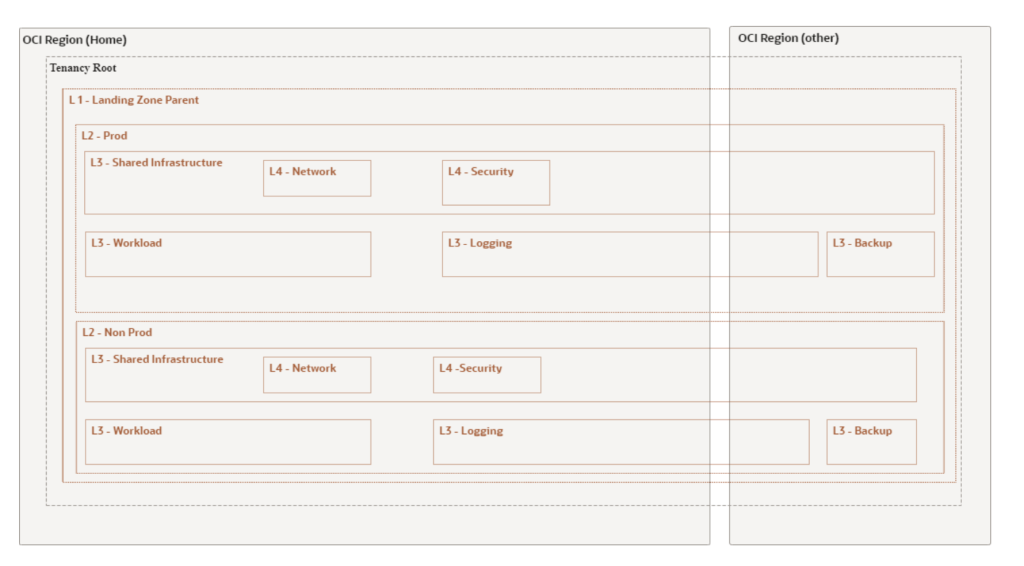
a. OELZ v2 Landing Zone Module
This module orchestrates the entire landing zone creation process. It invokes the Environment module twice to establish two isolated environments (production and non-production) and creates the parent compartment for the landing zone.
b. Environment Module
The Environment module aggregates other modules to form a single, isolated environment within the landing zone. It doesn’t create resources itself, but instead combines the functionalities of the following modules:
- Compartments module
- Budget and Tagging module
- Identity module
- Network module
- Security module
- Monitoring module
- Logging module
c. Compartments Module
This module creates a structured hierarchy of compartments within a single environment in OELZ v2. Compartments are fundamental building blocks in OCI, serving as logical containers for organizing and isolating your cloud resources. This isolation enhances security by allowing you to define granular access controls at the compartment level. The module creates a hierarchy of compartments, including:
- L2 – Environment: The top-level compartment encapsulating the entire environment.
- L3 – Shared Infrastructure: Contains resources shared across the environment.
- L4 – Network: Houses the hub component of the network architecture.
- L4 – Security: Contains security and identity-related components.
- L3 – Workload: Holds spoke compartments, each representing a separate workload or application.
- L3 – Logging: Stores log files generated within the environment.
- L3 – Backup: Contains configuration and state files for backup purposes.
By creating this compartment structure, OELZ v2 establishes a foundation for efficient resource management, access control, and security isolation.
d. Budget and Tagging Module
This module is optional and focuses on cost management and governance within OELZ v2. It provides tools to help you track and control your cloud spending.
- Budget Module: Allows you to set budgets for each environment at the L2-Environment compartment level. You can receive alerts when your spending approaches or exceeds these limits, helping you avoid unexpected costs.
- Tagging Module: Enables you to assign metadata (tags) to your cloud resources, such as their purpose, owner, or environment. Tags help you organize, manage, and track costs associated with your resources. OELZ v2 creates a tag namespace per environment in the L2-Environment compartment, with default tags for Environment, Cost Center, and Geo Location.
By utilizing budgeting and tagging, you can gain better visibility into your cloud costs, optimize resource utilization, and ensure adherence to your organization’s financial policies.
e. Identity Module
The Identity module is responsible for creating and configuring an identity domain within an environment in the landing zone. It establishes user groups with specific permissions to access and manage different types of resources. These groups include:
- Network Admin: Access to network resources.
- SecOps Admin: Access to security-related resources.
- Identity Admin: Manages identity-related resources.
- Platform Admin: Access to usage reports and budget management.
- Ops Admin: Access to metrics, events, and alerts.
- Log Admin: Access to log data.
By defining these groups and their associated policies, OELZ v2 ensures that only authorized personnel can perform actions on specific resources, adhering to the principle of least privilege and enhancing security.
f. Monitoring Module
The Monitoring module enables you to monitor the health and performance of your OELZ v2 environment. It leverages OCI services to collect metrics and events, which can be used to create alerts and dashboards.
Key features of the Monitoring module include:
- Alert Channels: Create notification topics (e.g., PRD-Network-Critical, NPRD-Security-Warning) and subscriptions (e.g., email) to receive alerts about specific events or conditions.
- OCI Service Incidents: Subscribe to console announcements to stay informed about OCI service incidents and required actions.
- Cloud Guard and Vulnerability Scanning: Monitor the status of Cloud Guard and Vulnerability Scanning to detect security threats and vulnerabilities.
- Metrics-Based Monitoring: Enable monitoring of Network, Security, Logging, and Workload compartments by creating alarm rules for service metrics.
- OCI Logging Analytics: Enable Logging Analytics for reporting and analysis through Log Explorer and Dashboards.
The Monitoring module provides a comprehensive view of your OELZ v2 environment, allowing you to proactively identify and address issues, optimize performance, and ensure the security and compliance of your cloud resources.
g. Network Module
The Network module is the backbone of OELZ v2, establishing the network architecture with a hub-and-spoke design. This design enhances security by isolating workloads within separate “spoke” VCNs while centralizing shared services in the “hub” VCN.
Key features include:
- Hub VCN: Contains public and private subnets for internet-facing resources and shared services. It also includes a Dynamic Routing Gateway (DRG) for connectivity to spokes and optional components like an internet gateway, NAT gateway, and service gateway.
- Spoke VCNs: Each spoke is an isolated VCN for specific workloads, connected to the hub via VCN attachments. Spokes can have their own NAT and service gateways.
- VCN Peering: Enables private communication between VCNs without traversing the internet.
- Network Extension Module: Optionally deploy Site-to-Site VPNs in each environment or share a FastConnect circuit between environments.
h. Security Module
The Security module prioritizes the protection of your OCI environment by implementing security best practices and services. It aligns with Oracle’s security-first cloud strategy, emphasizing simplicity, guidance, integration, automation, and cost-effectiveness.
Key features include:
- Cloud Guard: Monitors for threats and misconfigurations, providing alerts and remediation guidance.
- Vulnerability Scanning: Scans hosts, open ports, and container images for vulnerabilities.
- Vault (Key Management): Securely stores and manages encryption keys and secrets for OCI resources and logs.
- Bastion: Provides restricted and time-limited access to private resources without public endpoints.
- Network Firewall: Offers visibility and control over traffic entering and within your cloud environment.
i. Logging Module
The Logging module is responsible for capturing and managing log data from various sources within your OELZ v2 environment. It centralizes logs, making them easily accessible for analysis, troubleshooting, and security monitoring. The module can be configured to collect logs from OCI services, custom applications, and other sources.
j. Workload Module
The Workload Expansion module simplifies the deployment of resources for new workloads within the OELZ v2 framework. It creates a dedicated compartment for the workload, sets up the network spoke, and configures logging and monitoring.
Key features include:
- Compartment: A dedicated compartment for the workload within the L3 – Workload compartment.
- Network (Spoke): A VCN with private subnets for different application tiers (Web, App, DB), connected to the hub DRG.
- Logging: Captures logs from the workload expansion.
- Monitoring: Sets up monitoring and alerting for the workload resources.
- Policies and Workload Group: Creates admin groups with specific permissions for managing the workload resources.
6. Deploying Oracle Enterprise Landing Zone v2 (OELZ v2)
OELZ v2 can be deployed whether you have existing infrastructure in OCI or are starting from scratch. If you have existing infrastructure, it is recommended to create a new child tenancy (a separate, isolated environment within your main OCI tenancy) to avoid conflicts. Child tenancies have their own resource limits, so ensure they meet the requirements for deploying OELZ v2.
You can deploy OELZ v2 using either Oracle Resource Manager or Terraform CLI. Below are the high-level steps, but it is advised to check the OELZ v2 deployment documentation for the latest detailed steps.
Deploying with Terraform CLI
- Install Terraform: Ensure you have Terraform 1.0.0 or later installed.
- Set up API Keys: Follow instructions to obtain the required keys and OCIDs for your OCI account.
- Clone the Template: Clone the Terraform template from the GitHub page.
- Initialize the Working Directory: Navigate to the cloned directory and run
terraform initto initialize the Terraform working directory. - Create and Populate terraform.tfvars: Create this file in the cloned directory and fill in the required variables. Refer to the OELZ v2 Configuration and Input Variables Reference in the README for guidance.
- Run Terraform Commands: Execute
terraform planto review the planned changes, and thenterraform applyto deploy OELZ v2.
Deploying with Resource Manager
- Navigate to Resource Manager: Go to Developer Services -> Resource Manager -> Stacks in the OCI console.
- Create Stack: Choose the compartment and select “Create stack.”
- Select Source: Choose “Source code control system” for the Terraform source.
- Configure Stack: Select GitHub as the source, the
oci-landing-zonesrepository,mainbranch, andtemplates/enterprise-landing-zoneas the working directory. Choose the appropriate Terraform version. - Enter Variable Values: Provide values for variables as prompted. Refer to the OELZ v2 Configuration and Input Variables Reference.
- Review and Create: Review the stack values and click “Next” to create.
- Manage Stack: Use the buttons on the Stack page to plan, apply, or destroy your stack.
Tearing Down an OELZ v2 Stack
Due to dependencies, tearing down an OELZ v2 stack requires a manual process:
- Clean Up Resources:
- Delete retention rules and objects in audit, default, service event, and archive buckets.
- Deactivate and delete identity domains for each environment.
- Delete vaults and keys (consider the 7-day waiting period for vault deletion).
- Purge logs in Logging Analytics and optionally delete the group.
- Delete with Terraform: After manual cleanup, use Terraform to delete the remaining OELZ v2 resources.
Remember to consult the official OELZ v2 documentation for detailed instructions and troubleshooting. The steps might change as Oracle develops new process.
7. Oracle Multicloud Design Choices
If you’re using Oracle Database and considering Microsoft Azure for your cloud needs, Oracle offers several ways to integrate the two seamlessly. This gives you the flexibility to leverage Oracle’s powerful database technology within Azure’s cloud environment.
Read: Azure Cloud Landing zone architecture
Here are the three main options Oracle provides:
- Oracle Database@Azure: This lets you create and manage Oracle Databases directly within Azure. Azure handles the billing, and most support comes from Azure, with Oracle helping with database-specific questions. This option simplifies the deployment process and allows organizations to leverage Azure’s familiar tools and services while benefiting from the performance and reliability of Oracle Database.
- Cross-cloud connection to Azure: This is a direct, private link between Oracle’s cloud and Azure. It’s faster and more secure than using the public internet for transferring data between the two. You can establish this connection using options like ExpressRoute or VPN, depending on your specific requirements for speed, security, and reliability.
- Oracle Database Service for Azure: This is a fully managed service where Oracle handles everything – the setup, maintenance, and updates of your Oracle Databases. You use an interface similar to Azure’s to manage your databases. This option is ideal for organizations that lack the in-house expertise to manage Oracle Databases or that want to focus on their core business rather than database administration. It’s particularly beneficial for use cases like development and testing environments, where ease of setup and management is a priority.
Which to Choose?
The best option for you depends on your needs:
- Oracle Database@Azure: Good for those who want to use Oracle Database within Azure and prefer Azure’s billing and support system.
- Cross-cloud connection to Azure: Ideal if you need a fast, secure way to connect applications and data between Oracle’s cloud and Azure.
- Oracle Database Service for Azure: Best for those who want a hassle-free experience where Oracle takes care of the technical details.
8. Advanced OELZ Configurations: Extending the Foundation
Oracle Enterprise Landing Zone v2 (OELZ v2) provides a robust foundation for deploying and managing workloads on Oracle Cloud Infrastructure (OCI). However, for complex deployments or specific organizational needs, advanced configurations can be implemented to further customize and extend OELZ v2 functionalities. Here’s an exploration of some advanced OELZ configurations:
-
Workload Expansion Templates:
OELZ v2 comes with pre-built Terraform modules for core functionalities. Workload expansion templates offer additional pre-configured modules for specific workload types, such as:
- Containerized Applications: Modules for deploying Kubernetes clusters and container registries.
- Big Data Workloads: Configurations for deploying and managing Apache Hadoop or Oracle Big Data Service.
- High Availability (HA) Deployments: Modules for setting up redundant resources for critical applications.
These templates expedite deployment by providing pre-defined configurations for specific workloads.
-
Exadata Expansion for High-Performance Computing:
For deployments requiring high-performance computing capabilities, OELZ v2 can be extended to integrate Oracle Exadata Cloud Service. Exadata offers a fully managed, high-performance platform optimized for running data warehouse, analytics, and high-performance computing workloads. OELZ v2 can be configured to provision and manage Exadata resources alongside other OCI resources within a compartment, ensuring consistent security and governance controls.
-
Advanced Security Configurations:
While OELZ v2 offers pre-built security policies, advanced configurations might be needed to address specific security requirements. This could involve:
- Implementing additional security zones within compartments for heightened segregation of duties and data sensitivity.
- Configuring more granular IAM policies and access controls based on the principle of least privilege.
- Integrating OELZ with advanced security solutions like Oracle Cloud Guard for continuous threat detection and automated remediation.
-
Federation with External Identity Providers:
OELZ v2 primarily uses OCI IAM for user authentication and authorization. However, for organizations with existing identity providers (IdPs) like Active Directory (AD), federation can be implemented. This allows users to access OCI resources using their existing AD credentials, simplifying user management and reducing the need for separate OCI accounts.
-
Multi-Region Deployments:
OELZ v2 deployments are typically designed for a single region. However, for disaster recovery or geographically distributed deployments, OELZ can be extended across multiple OCI regions. This requires careful configuration of disaster recovery strategies and network peering connections between regions to ensure seamless failover and data replication. It’s important to consider the increased complexity and potential cost implications of multi-region deployments.
Read: High Availability and Disaster Recovery
-
Disaster Recovery and High Availability:
OCI offers disaster recovery (DR) and high availability (HA) solutions that can be integrated with your OELZ v2. This may involve:
- DR Strategy Planning: Develop a DR strategy that defines recovery point objectives (RPOs) and recovery time objectives (RTOs) for your workloads.
- OCI DR Services: Configure OCI services like Data Guard for databases and Oracle Cloud Infrastructure Object Storage for backups to establish robust DR capabilities.
- HA Configurations: Implement HA configurations for critical workloads to ensure continuous operation in case of server failures.
-
Integration with Third-Party Tools:
OELZ v2 can be integrated with third-party tools for enhanced functionality. Examples include:
- Configuration Management Tools like Ansible or Chef for automating infrastructure provisioning and configuration.
- Security Information and Event Management (SIEM) systems for centralized security logging and analysis.
Integrating these tools allows you to leverage their capabilities within your OELZ v2 environment.
Considerations for Advanced OELZ Configurations:
- Implementing advanced configurations requires in-depth knowledge of OCI, Terraform, and OELZ architecture.
- Customization introduces complexity and requires ongoing maintenance.
- Careful planning, testing, and documentation are essential to ensure compatibility and avoid security vulnerabilities.
- Consider the potential impact on performance and cost when implementing advanced configurations.
OELZ v2 offers a flexible foundation that can be extended with advanced configurations to meet specific organizational requirements. By leveraging custom Terraform modules, Exadata integration, advanced security features, and multi-region deployments, organizations can further optimize their OELZ environment for secure and scalable cloud deployments on OCI. It’s important to weigh the benefits of customization against the added complexity and ensure you have the resources to manage it effectively.
9. Oracle Cloud Infrastructure (OCI) Landing Zone Best Practices
Oracle Cloud Infrastructure (OCI) Landing Zones provide a secure and scalable foundation for deploying your workloads in the cloud. They offer a set of pre-defined best practices, templates, and configurations that help you quickly establish a compliant and well-architected environment.
Here are some best practices to consider when implementing an OCI Landing Zone:
Planning and Design:
- Define Your Requirements: Clearly outline your business goals, technical requirements, and compliance needs before starting. This will help you choose the right Landing Zone architecture and configurations.
- Security First: Prioritize security throughout the design process. Implement security best practices like identity and access management (IAM), network security, and data encryption from the outset.
- Compartmentalization: Organize your resources into compartments based on their function, ownership, or project. This will help you manage access controls and resource quotas more effectively. For example, you can create separate compartments for development, testing, and production environments.
- Networking: Design a robust network topology that aligns with your security and performance requirements. Consider using virtual cloud networks (VCNs), subnets, security lists, and network security groups to control traffic flow. For instance, you might use security lists to restrict access to specific ports or protocols.
- Tagging: Implement a comprehensive tagging strategy to track your resources and costs. Tags can be used for filtering, reporting, and automation purposes. You could tag resources with information like the project name, environment, or owner.
Deployment and Configuration:
- Infrastructure as Code (IaC): Leverage IaC tools like Terraform or Ansible to automate the provisioning and configuration of your landing zone. This ensures consistency, repeatability, and easier management of your environment. For example, you could use Terraform to define your entire landing zone infrastructure in code, making it easy to replicate and modify.
- Automation: Automate repetitive tasks like patching, backups, and monitoring to reduce operational overhead and improve efficiency. This could involve using OCI’s automation tools or integrating with third-party solutions.
- Monitoring and Logging: Implement robust monitoring and logging solutions to track the performance, availability, and security of your resources. Use OCI services like Monitoring, Logging, and Cloud Guard for comprehensive visibility. For instance, you could set up alarms to notify you of unusual activity or performance issues.
- Cost Optimization: Regularly review your resource usage and optimize your cloud spending by utilizing reserved instances, spot instances, and other cost-saving measures. You could also use OCI’s Cost Analysis tool to identify areas where you can reduce costs.
- Governance: Establish clear governance policies and procedures for managing your landing zone. This includes defining roles and responsibilities, setting up change management processes, and ensuring compliance with industry standards and regulations. For example, you might require approval for any changes to the landing zone’s infrastructure.
Oracle-Specific Landing Zones:
- Oracle Enterprise Landing Zone (OELZ): This framework provides a comprehensive set of best practices and templates for deploying Oracle workloads in OCI. It covers areas like identity and access management, networking, security, and cost management. OELZ includes pre-built Terraform templates and modules to accelerate deployment and ensure adherence to Oracle’s best practices.
- Secure Cloud Computing Architecture (SCCA) Landing Zone: This framework is designed to meet the specific security requirements of the U.S. Department of Defense (DoD). It incorporates additional security controls and configurations to ensure compliance with DoD standards.
- CIS Foundations Benchmark Landing Zone: This template helps you align your OCI environment with the Center for Internet Security (CIS) Foundations Benchmark, a set of security best practices for cloud environments.
By following these best practices and leveraging the available landing zone frameworks, you can build a secure, scalable, and compliant OCI environment that supports your business objectives. Remember to continuously monitor, update, and adapt your landing zone to meet evolving requirements and address potential security risks.
10. Oracle Cloud Infrastructure (OCI) Landing Zone Checklist
Here’s a comprehensive OCI Landing Zone checklist to guide you through the planning, deployment, and ongoing management phases:
Planning & Design:
- Define Business Requirements:
- Identify workloads and applications to be migrated or deployed.
- Determine performance, scalability, and availability needs.
- Outline compliance and regulatory requirements.
- Choose Landing Zone Architecture:
- Evaluate Oracle Enterprise Landing Zone (OELZ) or create a custom design.
- Consider multi-region or single-region deployment based on resiliency needs.
- Determine network topology (VCNs, subnets, routing).
- Security & Compliance:
- Plan identity and access management (IAM) policies and roles.
- Define security lists, network security groups, and firewall rules.
- Address data encryption at rest and in transit.
- Implement security monitoring and incident response mechanisms.
- Cost Management:
- Estimate resource usage and establish budgets.
- Explore cost optimization options like reserved instances and spot instances.
- Set up cost tracking and reporting mechanisms.
Deployment & Configuration:
- Infrastructure as Code (IaC):
- Use Terraform or Ansible to automate provisioning and configuration.
- Maintain version control for IaC templates.
- Core Services:
- Deploy and configure VCNs, subnets, internet gateways, and NAT gateways.
- Set up load balancers, block storage, and object storage as needed.
- Implement identity providers (IdPs) for user authentication.
- Security Configuration:
- Enable security services like WAF, DDoS protection, and Cloud Guard.
- Configure security lists and network security groups to restrict traffic.
- Set up security monitoring and alerting.
- Monitoring & Logging:
- Deploy OCI Monitoring and Logging services to track resource health and performance.
- Set up alarms and notifications for critical events.
- Enable audit logging for compliance and security purposes.
Ongoing Management:
- Patch Management:
- Regularly apply security patches and updates to OCI resources.
- Use automation tools to streamline patching processes.
- Backup & Disaster Recovery:
- Implement regular backups for critical data and resources.
- Set up disaster recovery (DR) strategies and test them regularly.
- Cost Optimization:
- Continuously monitor resource usage and identify optimization opportunities.
- Utilize cost-saving features like auto-scaling and scheduling.
- Governance & Compliance:
- Enforce tagging policies for resource tracking and cost allocation.
- Regularly review IAM policies and roles to ensure least privilege access.
- Perform periodic security audits and vulnerability assessments.
Additional Considerations:
- High Availability: Design for high availability (HA) to minimize downtime and ensure business continuity.
- Performance Optimization: Optimize network performance, storage configurations, and database tuning.
- Automation: Automate routine tasks to reduce operational overhead and minimize errors.
- Documentation: Maintain detailed documentation of your landing zone architecture, configurations, and processes.
By following this checklist and adhering to OCI best practices, you can create a well-architected landing zone that provides a solid foundation for your cloud initiatives. Remember that this is a living document, and it should be updated as your requirements and OCI services evolve.
11. Summary
In this technical deep dive, we’ve explored the intricacies of Oracle Cloud Landing Zones (OCLZs), focusing on the significant advancements in OELZ v2. We’ve dissected its modular architecture, emphasizing the flexibility and scalability it offers for tailoring your cloud environment to your specific needs. We’ve also highlighted the robust security features, improved identity management, and streamlined user experience that make OELZ v2 a compelling choice for modern cloud deployments.
We’ve walked through the functional modules that constitute OELZ v2, from compartmentalization and cost management to identity, networking, security, monitoring, logging, and workload management. Each module plays a crucial role in establishing a well-organized, secure, and efficient cloud foundation. Additionally, we’ve outlined the deployment process using both Terraform CLI and Resource Manager, providing you with the tools to get started.
12. Conclusion
As cloud architects and engineers, you understand the importance of a solid foundation for your cloud infrastructure. OELZ v2 empowers you to build that foundation on OCI with confidence. Its modularity, security enhancements, and automation capabilities align with modern cloud best practices, enabling you to create a cloud environment that is not only secure and compliant but also adaptable to your evolving needs.
Whether you’re starting fresh or migrating from OELZ v1, the transition to OELZ v2 is a strategic move towards a more agile and resilient cloud infrastructure. By embracing OELZ v2 and its advanced configurations, you can unlock the full potential of OCI and drive innovation within your organization.
Remember, the cloud landscape is constantly evolving. Stay informed about the latest OELZ updates and best practices to ensure your cloud environment remains at the forefront of technology and security.