A Google Cloud Landing Zone (LZ) provides organizations with a well-architecture foundation upon which organization can securely build, operate, and scale their cloud workloads. Landing zones help enterprises to deploy, use, and scale Google Cloud services more securely. Landing zones are dynamic and grow as the enterprise adopts more cloud-based workloads over time.
A landing zone spans multiple areas and includes different elements, such as identities, resource management, security, and networking. Many other elements can also be part of a landing zone. This blog post presents the key concepts of a Google Cloud Landing Zone, its essential components, design considerations, and strategies for implementation within Google Cloud Platform (GCP).
1. Google Cloud Landing Zone Introduction
A Google Cloud Landing Zone is a preconfigured environment comprising a set of cloud resources, governance policies, and best practices tailored to an organization’s specific requirements. It facilitates secure, compliant, and scalable cloud deployments, providing a strong basis for workload migration and innovation.
A Google Cloud Landing Zone (LZ) isn’t just a pre-built environment – it’s a strategic investment that unlocks the full potential of Google Cloud Platform (GCP). Here’s how Landing zone leverage GCP’s unique features to deliver significant benefits:
Read: What is a cloud Landing zone and why it is important.
- Seamless Integration with GCP Services: Landing Zones are designed to seamlessly integrate with core GCP services like Cloud IAM, Cloud Monitoring, and Cloud Logging. This ensures that security policies, access controls, and monitoring solutions are natively integrated with your cloud environment, simplifying management and maximizing visibility.
- Leveraging Infrastructure as Code (IaC): GCP Landing Zones often utilize tools like Terraform or Cloud Deployment Manager. These tools allow you to define your LZ infrastructure as code, enabling automated and repeatable deployments. This approach minimizes configuration errors, promotes consistency, and facilitates faster rollouts.
- Harnessing GCP’s Security Features: Landing Zones exploit GCP’s built-in security features like Cloud Key Management Service (KMS) for encryption key management and Cloud Identity and Access Management (CIAM) for centralized user authentication. This integration simplifies security configuration and strengthens your overall security posture.
- Cost Optimization with GCP Billing Features: Landing Zones can leverage granular billing features within GCP to optimize cloud spending. Features like resource tagging and project hierarchy enable cost allocation to specific departments or projects, providing clear cost visibility and facilitating informed spending decisions.
- Scalability with Cloud Build and Containerization: Google Cloud Landing Zones can be designed to support containerized deployments using Cloud Build and Cloud Run. This approach promotes effortless scaling of applications based on demand, ensuring your cloud environment can grow alongside your business.
Beyond the Generic: Benefits Tailored to GCP
While some benefits of Landing Zones are universal, utilizing GCP specifically unlocks additional advantages:
- Fast Track to Anthos Migration: Landing Zones can be designed to streamline the migration process for existing workloads to Anthos, Google’s hybrid and multi-cloud platform. This allows organizations to leverage the benefits of GCP across their entire IT infrastructure.
- Simplified BigQuery Integration: Pre-configured network configurations within LZs can facilitate seamless integration with BigQuery, Google’s data warehouse solution. This enables efficient data ingestion and analysis for data-driven decision making.
- Unlocking AI and Machine Learning: Landing Zones can be configured to support Google Cloud AI Platform and Vertex AI, simplifying the deployment and management of AI and machine learning workloads. This empowers organizations to leverage the power of AI within their cloud environment.
In conclusion, a Google Cloud Landing Zone goes beyond pre-configuration. It’s a framework specifically designed to harness the strengths of GCP, accelerating cloud adoption, enhancing security, improving governance, achieving effortless scalability, and optimizing your cloud investment.
2. Sample GCP Landing Zone Architecture & Key Components
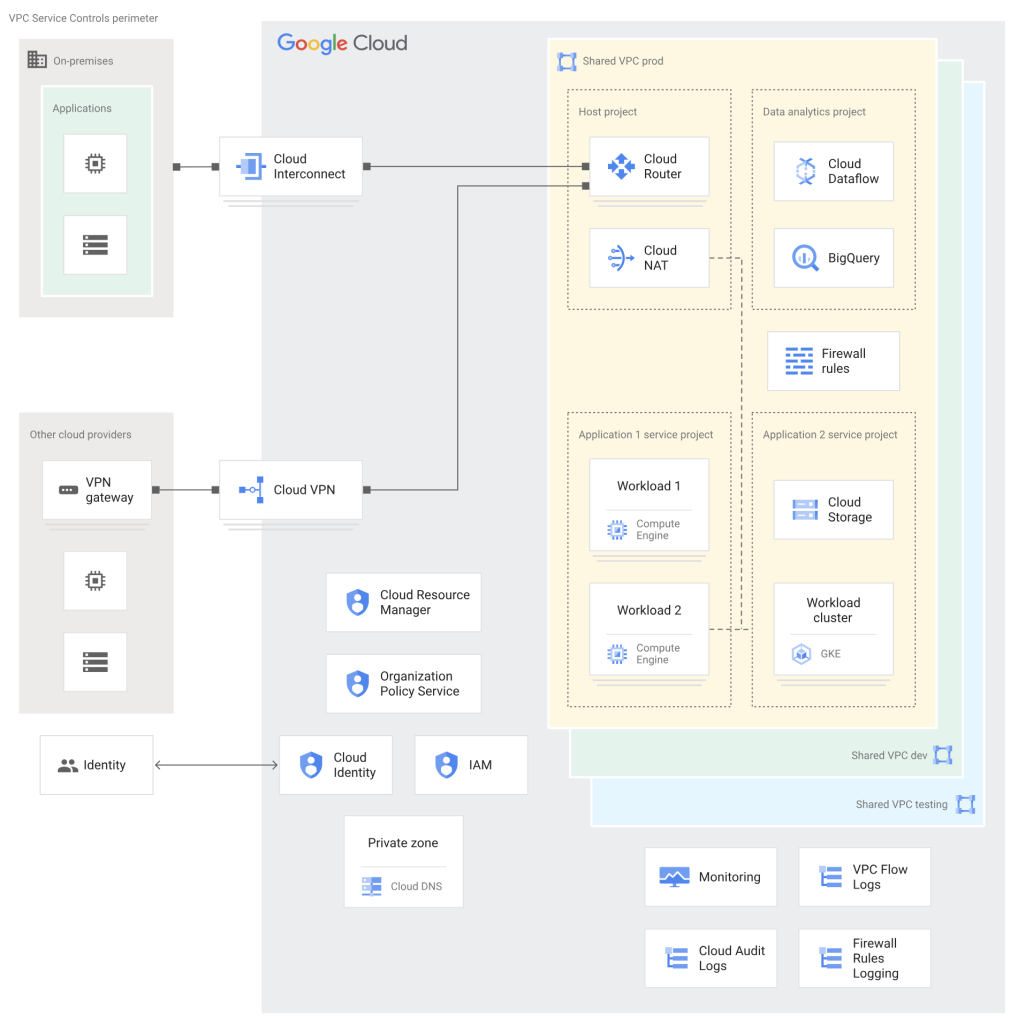
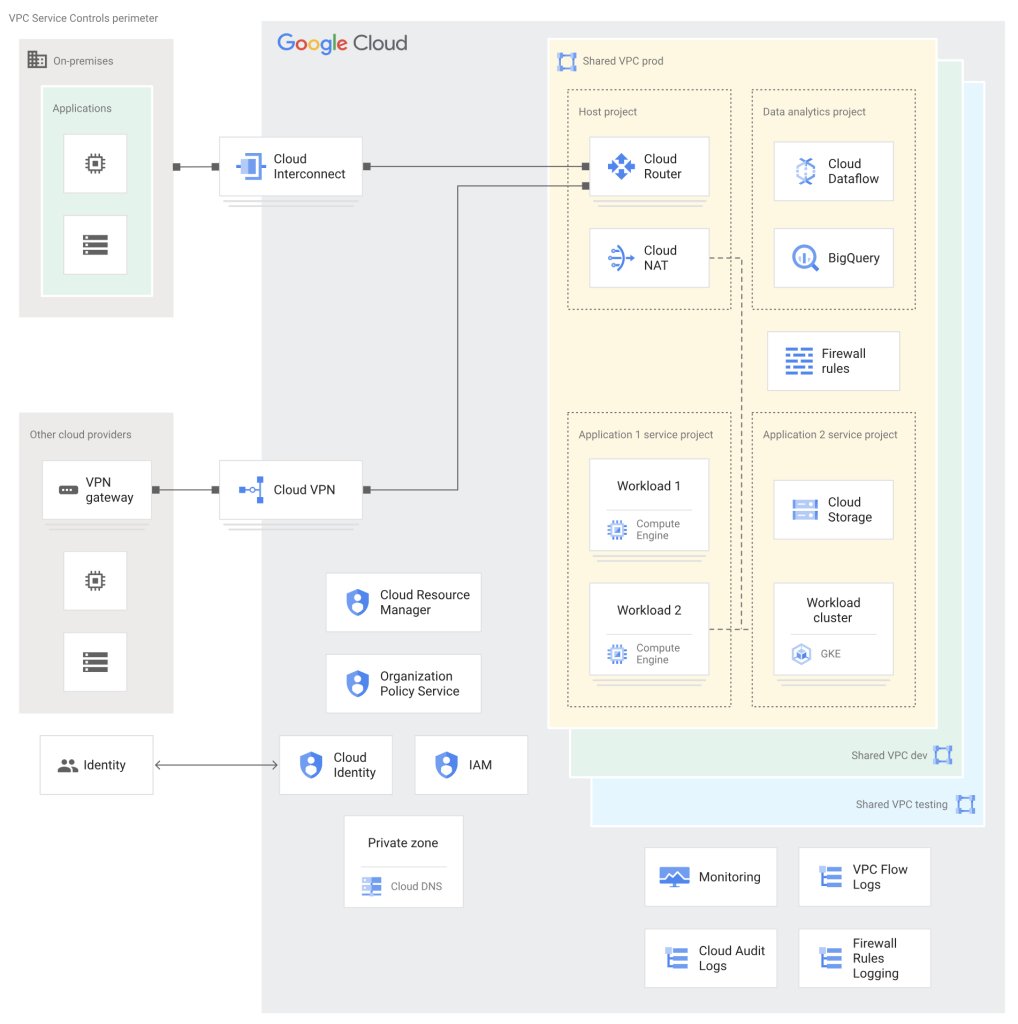
Landing zones are modular and built to grow. Your initial design can be expanded upon later. Design your landing zone with future growth in mind. Connectivity to on-premises environments can be added as needed. The diagram below outlines a sample Google Cloud Landing Zone (LZ) architecture designed for an Infrastructure as a Service (IaaS) use case with hybrid cloud and on-premises connectivity.
Key Components:
- Resource Hierarchy: Resource Manager defines a structured organization with policies for managing GCP resources.
- Identity and Access Management (IAM): Cloud Identity account integrates with on-premises identity providers to offer granular access control. This means users can log in with their existing credentials, simplifying the management of access across cloud and on-premises systems.
- Networking:
- Shared VPC networks (production, development, testing) connect resources across projects.
- VPC firewall rules govern inbound and outbound traffic.
- Cloud NAT enables outbound internet access for resources without external IPs.
- Cloud Interconnect (Dedicated or Partner) facilitates connectivity with on-premises environments.
- Cloud VPN provides connections to other cloud providers.
- Cloud DNS private zone hosts internal DNS records.
- Service Projects: Leverage Shared VPC networks for application resources.
- Observability:
- Cloud Monitoring and Logging track resource activity.
- Additional logging features (e.g., Audit Logs) ensure comprehensive data collection.
- VPC Service Controls Perimeter: A security zone isolates services and resources, mitigating data exfiltration risks.
Important Notes:
- Flexibility: This diagram is one example for an IaaS use case. Landing Zones can be adapted for PaaS, serverless, or other workload types.
- Automation: Tools like Terraform or Cloud Deployment Manager can automate the creation and management of these LZ components.
Multiple Workloads, Multiple Landing Zones?
Sometimes, different types of workloads have vastly different security, scaling, or compliance requirements. In those cases, it might make sense to have multiple LZs: a general one for most of your workloads, and a specialized LZ for those with unique needs. Certain resources like billing and user identities can still be shared between these landing zones.
Read: The complete guide on AWS Landing Zone Architecture
While this sample architecture provides a robust starting point, it’s only the beginning. A well-designed Landing Zone serves as the foundation for addressing critical aspects like security, governance, scalability, and compliance. In the next section, we’ll explore these design considerations in more detail.
3. Google Cloud Landing Zone Core Elements
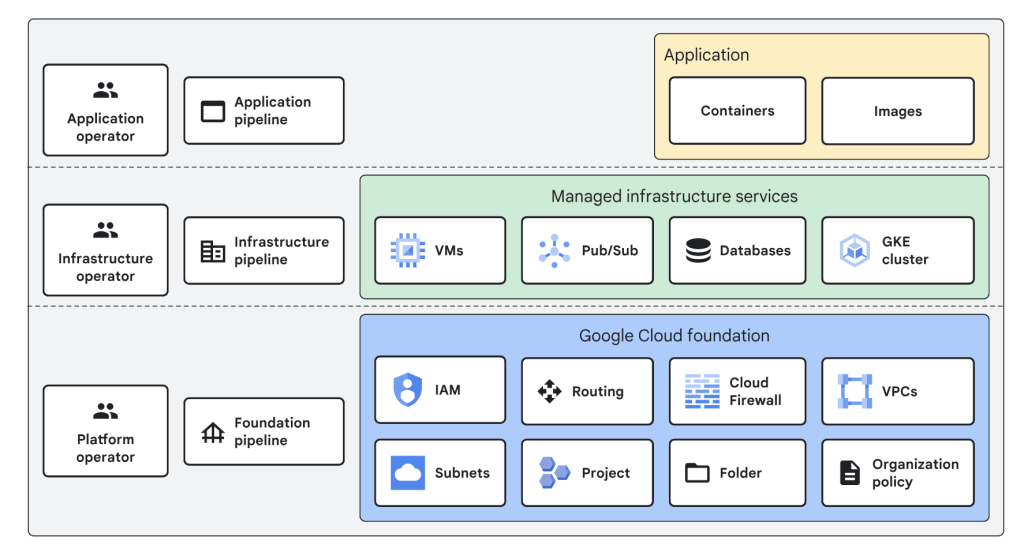
A well-designed Google Cloud Landing Zone (LZ) begins with a solid foundation. This includes managing user identities and access (Identity Provisioning), organizing resources logically (Resource Hierarchy), building a secure and flexible network, and implementing robust security controls. Such an LZ forms a secure and scalable base for your cloud workloads.
Let’s break down each of the core GCP Landing Zone elements at high level:
1. Identity Provisioning
- What it is: Controlling who can access your Google Cloud environment and what they’re allowed to do.
- Why it matters: A strong identity system is the cornerstone of security, preventing unauthorized access and easing team management.
- Tools to use:
- Cloud Identity: Google’s identity management solution, often synced with existing systems.
- Identity & Access Management (IAM): Lets you create fine-grained access policies.
2. Resource Hierarchy
- What it is: How you organize projects and folders within Google Cloud, similar to a company’s organizational chart. [Refer to Resource Hierarchy diagram from Section 2]
- Why it matters:
- Separation of concerns: Isolate production from development or different teams.
- Policy enforcement: Set rules once at a higher level to save time and prevent errors.
- Cost tracking: Link folders to billing to monitor spending by areas of your business.
- Tools to use: Resource Manager
3. Network
- What it is: Virtual Private Clouds (VPCs), subnets, firewall rules, and how everything connects within Google Cloud and externally. Think of it as the layout of your virtual data center. [Refer to Networking components in Section 2 diagram]
- Why it matters:
- Security: Firewall rules stop unwanted traffic, while network segmentation controls internal movement.
- Performance: Ensures applications communicate quickly and reliably.
- Hybrid Cloud: Seamlessly connect on-premises resources and other cloud providers.
- Tools to use:
- VPC Networking
- Cloud NAT
- Cloud DNS
- Cloud Interconnect
- Cloud VPN
4. Security Controls
- What it is: Going beyond basic IAM, this includes encryption standards, monitoring, alerting, and policies to prevent data from leaving where it shouldn’t. [Refer to VPC Service Controls Perimeter in Section 2]
- Why it matters: Every organization has to be security-conscious. A well-designed LZ includes security tools out of the box.
- Tools to use:
- Security Command Center
- Cloud Audit Logs
- VPC Service Controls
4. Additional GCP Landing Zone elements
To take your Landing Zone further, consider incorporating additional elements.
1. Monitoring and Logging
- What it is: Continuous tracking of your cloud environment’s health, performance, and security through metrics, logs, dashboards, and alerts.
- Why it matters:
- Troubleshooting: Quickly identify the root cause of issues.
- Proactive Maintenance: Prevent problems by spotting resource bottlenecks early.
- Security & Compliance: Maintain an audit trail of activity.
- Tools to use:
- Cloud Monitoring
- Cloud Logging
- Cloud Operations Suite
2. Backup and Disaster Recovery
- What it is: Processes and tools to protect your data and ensure applications remain operational, even in the face of unexpected events.
- Why it matters:
- Data protection: Prevents loss of important information.
- Business continuity: Keeps cloud applications serving customers, minimizing downtime.
- Compliance: Many industries have regulations about data retention and recovery.
- Tools to use:
- Snapshots
- Cloud Storage
- Disaster recovery solutions (various levels of complexity.
3. Compliance
- What it is: Adhering to regulations and standards governing how you handle data based on your industry (healthcare, finance, etc.) and where you operate.
- Why it matters:
- Avoiding fines and penalties: Non-compliance can result in significant costs.
- Customer trust: Demonstrate your commitment to data protection.
- Tools to use:
- Security Command Center
- Resource Manager
- Third-party solutions specializing in specific regulations
4. Cost Efficiency and Control
- What it is: Managing Google Cloud spending to maximize the value of your investment.
- Why it matters: Cloud costs can escalate quickly without proper management.
- Tools to use:
- Billing reports and dashboards
- Budgets and alerts
- Resource tagging
- Right-sizing recommendations
5. API Management
- What it is: Controlling and securing how applications interact within your cloud and externally.
- Why it matters:
- Security: Prevent unauthorized access to sensitive data and systems.
- Performance: Manage API traffic to avoid overloads.
- Monetization: Enable usage tiers and billing for public or partner APIs.
- Tool to use: Apigee
6. Cluster Management
- What it is: Managing fleets of virtual machines, especially for containerized applications (Kubernetes). This involves deployment, scaling, and updates.
- Why it matters: Running complex applications at scale requires automation.
- Tool to use: Google Kubernetes Engine (GKE)
Read: Know these 8 key design principles to build robust Cloud architectures
With a solid grasp of the essential Landing Zone elements, let’s delve deeper. In the next section, we’ll examine each element in more detail, exploring best practices, security considerations, and how to optimize each component within your Google Cloud environment.
5. Key Design Considerations for GCP Landing Zone Cloud Identity
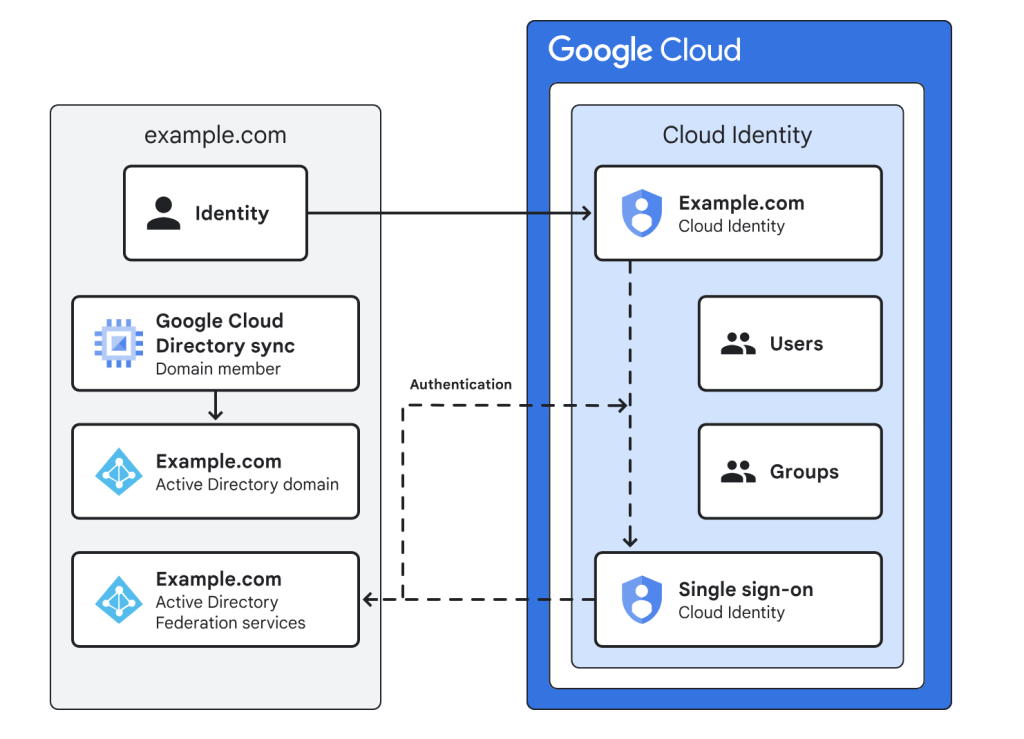
Identity and Access Management (IAM) is the foundation of security within your GCP Landing Zone. IAM determines who can access specific resources and what actions they’re authorized to perform. A well-designed Google Cloud Landing Zone incorporates robust Identity and Access Management (IAM) controls. In this section, we’ll delve into the key design considerations for GCP Cloud Identity, ensuring your LZ achieves a strong security posture
Key Decision Points for Cloud Identity
Consider two main options for designing your identity in GCP:
Option 1: Use Google as your primary Identity Provider
- Pros: Simpler management, native integration with Google Cloud IAM.
- Cons: Might need to migrate existing identities to Google Cloud, less flexibility if you have complex identity requirements.
- Suitable when: You’re a new organization, have a simple identity system, or want to minimize overhead.
Option 2: Use federation with an external Identity Provider
- Pros: Leverage your existing identity system, better for compliance or complex identity needs.
- Cons: More configuration complexity, potential added latency.
- Suitable when: You have an existing IdP, strict compliance needs, or complex identity requirements that aren’t easily met with Google as the primary IdP.
Read: Quick guide on Identity and Access Management important concepts
Identity Consolidation
If you have existing user accounts in other systems, you’ll need a consolidation strategy:
- Option 1: Consolidate a subset of accounts: Migrate relevant accounts to Google Cloud.
- Option 2: Consolidate all accounts through migration: Move all accounts to Google Cloud.
- Option 3: Consolidate all accounts through eviction: Don’t migrate existing accounts, and require new logins with Google Cloud identities.
Best Practices
- Least privilege: Give users and service accounts only the permissions they need.
- MFA: Enforce Multi-Factor Authentication for added security.
- Identity-Aware Proxy (IAP): Secure access to web applications without the need for a VPN.
- Regular Audits: Review IAM permissions and user accounts periodically.
Additional Considerations
- Workload Identity Federation: A way to securely authenticate workloads (applications, microservices) running in different environments to Google Cloud services, without managing service account keys.
- BeyondCorp Enterprise: Google’s implementation of a Zero Trust security model, providing context-aware access to resources.
6. Key design considerations for GCP Landing Zone Resource Hierarchy
A well-designed resource hierarchy in your Google Cloud Landing Zone is crucial for security, cost control, and operational efficiency. It determines how you organize projects, folders, and your organization node. Let’s explore key design considerations and best practices for creating this structure within GCP
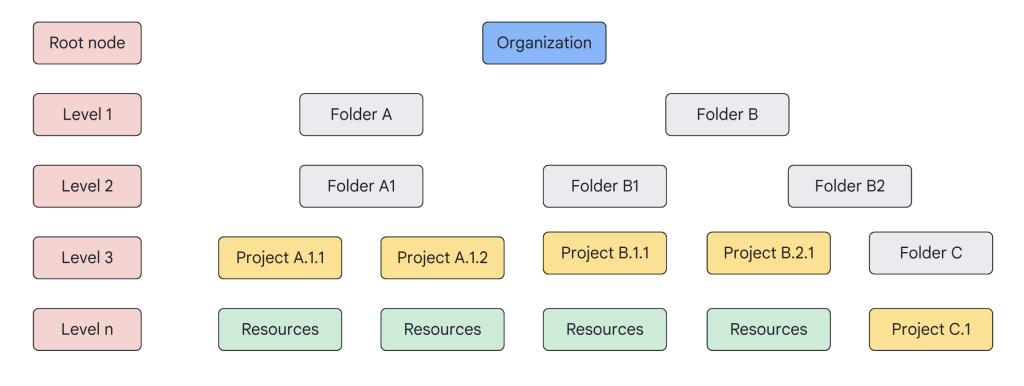
Designing an effective resource hierarchy is a fundamental step in building a well-structured and manageable Google Cloud environment. Your resource hierarchy refers to how you organize projects, folders, and your organization node into a logical structure. This structure influences everything from security policy enforcement to cost management and how your teams interact with GCP.
Google Cloud’s Resource Hierarchy
- The Organizational Root: Your Google Cloud resources exist in a hierarchy starting with an “Organization” node at the top. This usually represents your company or a major division.
- Folders: Allow you to group projects and other folders, creating logical subdivisions within your organization.
- Projects: The fundamental building block where your actual cloud resources (VMs, storage buckets, databases, etc.) reside. Projects are where you apply IAM permissions and billing is tracked.
Key Design Factors & Considerations
Resource hierarchy in Google Cloud platform should align with your organization’s way of working in the cloud, not just simply mirroring your corporate structure. Consider:
- Business Units or Functions: Group projects by teams, departments, or functional areas (e.g., HR, Finance, Marketing).
- Environments: Separate development, testing, and production environments into different folders or projects to manage access and prevent accidental changes.
- Application or Workload: Organize projects by individual applications or related sets of workloads.
- Security & Compliance: Structure the hierarchy to enforce different policies, compliance requirements, or levels of access control across your organization.
- Cost Allocation: Use projects and folders for more granular tracking and chargeback of cloud costs.
- Future Growth and Change: Design flexibility into the hierarchy to accommodate new teams, projects, or business requirements.
Different Types of Resource Hierarchies
Google Cloud offers flexibility, providing several hierarchy options such as environment-based, business unit-based, or even hybrid models. The key is to choose an approach that supports your organization’s specific needs and promotes long-term success within the cloud. There are several ways to approach your resource hierarchy, each with its own advantages and trade-offs:
Read: Cloud Architect’s guide to prevent vendor lockins
-
Environment-based Hierarchy: A common pattern where folders represent environments:
OrganizationProduction FolderDevelopment FolderTesting Folder
- Projects within each folder contain the resources for that specific environment.
- Pros: Clear separation, easy to understand, security policy alignment.
-
Business Unit-based Hierarchy: Folders reflect how your company is structured:
OrganizationMarketing FolderFinance FolderEngineering Folder
- Projects within could be per-team, per-application, etc.
- Pros: Aligns with company divisions, supports cost tracking by department.
-
Project-based Hierarchy: For smaller organizations or isolated workloads:
OrganizationProject AProject BProject C
- Pros: Simplest approach, suitable for small setups or experiments.
-
Hybrid Hierarchy: Combines aspects of above approaches:
OrganizationEnvironments FolderProductionDevelopment
Departments FolderSalesOperations
- Pros: Provides flexibility to fit complex requirements.
- Cons: More complex management if not carefully planned.
Important Note
- There’s no single “right” answer: The best hierarchy depends entirely on your company size, workload types, and how you work within Google Cloud.
- Google Cloud tools like Resource Manager make it possible to adjust your hierarchy over time if needed.
Best Practices
- Avoid overly complex hierarchies: Too many folders can introduce management overhead.
- Plan for governance: Establish policies around project creation and naming conventions.
- Iteratively refine: Re-evaluate your resource hierarchy as your Google Cloud use evolves.
- Leverage labels: Add labels to resources for additional organization and filtering options
7. Key Design Considerations for GCP Landing Zone Network
Your Google Cloud Landing Zone’s network is the foundation of its security and connectivity. Consider these key design considerations to create a network architecture that balances security, manageability, and scalability for your specific needs.
Key Decision Points
The central question is whether you want a centralized or decentralized control model for your network:
- Centralized Control: Offers greater visibility and control over network traffic and security, often preferred in environments with strict compliance requirements.
- Decentralized Control: Provides more autonomy to individual teams or projects, potentially leading to faster iteration but requiring coordination to maintain network consistency.
GCP LZ Network Design Options
Google Cloud offers several common network design approaches:
1. Shared VPC Network for Each Environment
- Simple setup: Individual Shared VPCs for development, testing, and production.
- Isolation: Environments are completely isolated from each other.
- Best for: Organizations starting on Google Cloud with simple networking needs.
2. Hub-and-Spoke Topology with Centralized Appliances
- Centralized Control: Network appliances (firewalls, VPN gateways) are deployed in a hub VPC for control and inspection. Spoke VPCs connect to the hub.
- Cost-Efficient: Appliances are shared across multiple workloads.
- Best for: Strict security requirements and easier management of network traffic.
3. Hub-and-Spoke Topology Without Appliances
- Flexibility: No centralized network appliances. Connectivity is achieved with VPC Peering or Cloud VPN.
- Scalability: Easy to add spoke networks without the limitations of centralized appliances.
- Best for: Dynamic workloads or where cost-efficiency is prioritized over centralized control.
4. Expose Services in a Consumer-Producer Model with Private Service Connect
- Secure Service Consumption: Services are privately exposed from a producer VPC and consumed with Private Service Connect in consumer VPCs.
- Traffic Isolation: No direct connectivity between VPCs.
- Best for: Highly sensitive services or scenarios with strict data access requirements.
Read: Cloud Networking Basics and Fundamentals
Here’s a summary of common design patterns, emphasizing their advantages, drawbacks, and typical use cases:
| Network Design | Pros | Cons | Ideal Use Case |
|
Shared VPC Per Environment |
Simple to set up, complete isolation | Scaling limitations, potential IP range overlap | Small organizations, simple use cases |
| Hub-and-Spoke (Centralized) | Centralized control, cost-efficient appliances | Can become a bottleneck, complex setup | Strict security, shared appliances across workloads |
| Hub-and-Spoke (Decentralized) | Scalable, flexible, no centralized bottleneck | Requires coordination, potentially less control | Rapid growth, dynamic workloads, cost-efficiency focus |
| Private Service Connect | Strong security, granular service access | Complex to manage, potential performance overhead | Sensitive services, strict data privacy requirements |
Additional Considerations
- Hybrid Cloud Connectivity: Do you need connections to on-premises networks? (Cloud VPN, Dedicated Interconnect, Partner Interconnect)
- Security & Compliance: Specific firewall requirements, traffic inspection needs, or data residency constraints.
- Global Workloads: Network performance and latency if you have deployments across multiple regions.
Choosing the Right Design
No single network design is universally best. Consider these factors to make an informed decision:
- Organization Size and Structure: Smaller organizations might favor simple designs, while larger ones might need more advanced control.
- Security & Compliance: Stricter requirements might necessitate centralized control models.
- Management Overhead: More complex network designs require greater operational effort.
- Cost: Centralized appliances can be cost-efficient, but factor in their potential limitations.
GCP Network Implementation Steps – Highlevel
The first step in implementing your Google Cloud landing zone network is meticulous planning. Determine the number of VPCs (Virtual Private Clouds) needed and carefully allocate IP address spaces for each VPC and its subnets. Pay close attention to firewall rules. Begin with a restrictive baseline that denies most traffic, then selectively open only the specific ports and protocols essential for application functionality.
If your setup requires a connection to an existing on-premises network, select between Cloud VPN for smaller data flows or Cloud Interconnect for high-bandwidth, low-latency workloads. Configure the relevant components on both Google Cloud and your on-premises network accordingly. Here are the high-level steps
- Create VPC Networks: For each VPC required in your design (hub, spokes, shared VPCs), create a custom VPC with the necessary subnets and IP ranges.
- Set up Peering/VPN (If Needed):
- Hub-and-Spoke: Establish VPC Peering or Cloud VPN connections between hub and spoke VPCs.
- Firewall Rules: Configure firewall rules to control inbound and outbound traffic, particularly if you have a centralized hub with appliances.
- Private Service Connect (If Needed): Enable Private Service Connect and configure endpoints if you’re adopting this model for service communication.
- External Access Controls: Use Cloud NAT, VPN, or other appropriate methods if you require access to Google Cloud resources from the internet or on-premises networks.
- Organization Policies: Enforce constraints on VPC creation, IP ranges, and other networking parameters using organization policies for better governance.
For enhanced security, consider tools like Cloud Armor for DDoS protection and VPC Service Controls to create secure perimeters around sensitive Google Cloud services. Remember, this is a simplified overview; refer to official Google Cloud documentation for detailed instructions. The optimal network design is the one that best aligns with your unique organizational needs, balancing factors like security, operational complexity, and isolation requirements.
7. Key Design Considerations for GCP Landing Zone Security
A well-designed Google Cloud Landing Zone prioritizes security from the ground up. Let’s explore key areas to ensure your Landing Zone offers robust protection:
1. Limiting Service Account Credentials
- Workload Identity Federation: Minimize risks by authenticating workloads to GCP services without long-lived keys.
- Short-Lived Credentials: Use temporary OAuth 2.0 tokens or rotate service account keys frequently.
- Secrets Management: Store sensitive keys securely with Cloud Secret Manager.
2. Data Exfiltration Controls
- VPC Service Controls: Secure sensitive Google services (BigQuery, Cloud Storage, etc.) with security perimeters.
- Data Classification & DLP: Identify sensitive data, apply labels, and use Cloud Data Loss Prevention to block unauthorized access attempts.
- API Monitoring: Use Apigee or similar tools to detect unusual API usage that might indicate data exfiltration.
3. Continuous Threat Monitoring
- Security Command Center: Google’s central dashboard for monitoring and detecting threats across your GCP environment.
- Config Validator: Use policy-as-code to enforce desired configurations and alert on deviations.
- Third-Party Tools: Integrate with GCP for advanced vulnerability scanning and threat detection.
4. Centralized Logging
- Cloud Logging: Store and analyze logs from GCP services, custom apps, and even 3rd-party sources.
- Cloud Operations Suite: Advanced capabilities on top of Cloud Logging, including filtering, alerting, and dashboards.
- SIEM Integration: Export logs to your existing SIEM solution for a unified security analytics view.
5. Encryption at Rest
- Consider Compliance Needs: Determine your encryption strategy based on regulations and data sensitivity.
- Customer-Supplied Encryption Keys (CSEK): Full control over encryption, but you manage the keys.
- Customer-Managed Encryption Keys (CMEK): Integration with Cloud KMS for key management.
- Google-Managed Keys: Simplest option, but less control for strict compliance scenarios.
6. Encryption in Transit
- Google-Managed TLS Certificates: Google handles certificate management for many services.
- Certificate Authority Service: Manage your own certificates or integrate with 3rd-party authorities.
7. Controlling Cloud Provider Access
- Restrict IAM Roles: Limit GCP support personnel permissions to the bare minimum.
- Auditing and Logging: Track GCP support actions within your project.
- Access Approvals: Implement workflows for approving privileged actions by GCP support.
Essential Security Measures
- Implement Workload Identity Federation or short-lived credentials to minimize service account key risks.
- Enforce continuous monitoring with Security Command Center and Cloud Logging.
- Encrypt data at rest and in transit using Google-managed solutions or by supplying your own keys.
Read: Cloud Security Basics and Fundamentals
Remember: Security is an ongoing process. Employ a defense-in-depth strategy, align with compliance requirements, and regularly review your security posture as your GCP usage evolves.
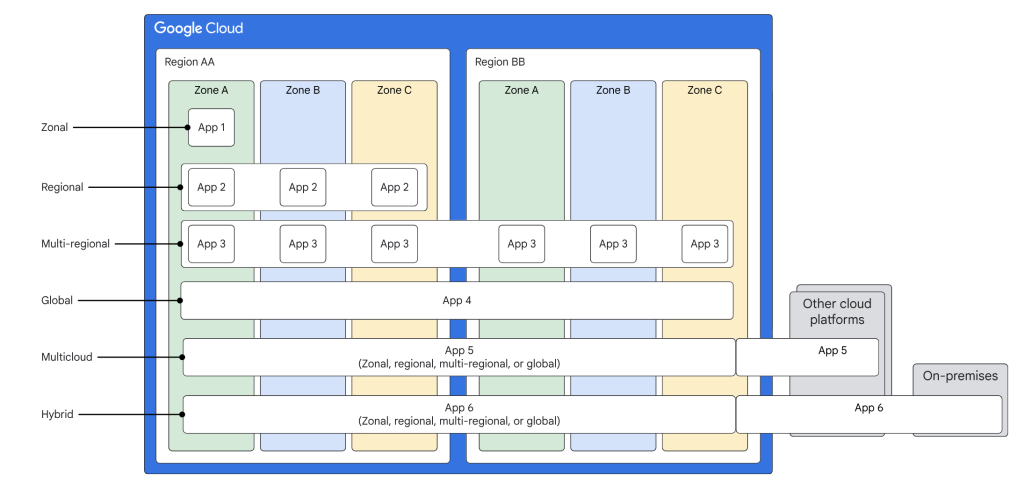
8. Application Deployment archetypes in GCP
When designing your GCP Landing Zone, consider the best way to deploy your applications to meet your specific needs. A deployment archetype is a blueprint for how you distribute application components across geographic regions. Choose an archetype based on factors like
- Availability: How crucial is it for your application to be always accessible?
- Latency: How quickly do users, especially those in diverse locations, need responses?
- Cost: Are you budget-sensitive, or is maximum availability your top priority?
- Regulatory Needs: Are there data sovereignty regulations to follow?
Read: High availability vs Fault Tolerance vs Disaster Recovery
Types of Deployment Archetypes
- Zonal App Deployment
-
- What it is: All your application components run within a single Google Cloud zone (a zone is like a single data center).
- Simple Example: A basic website with a database, running entirely within the “us-central1-a” zone.
- Pros: Simplest to manage, low cost
- Cons: If that zone has an outage, your application is down.
- Regional App Deployment
-
- What it is: Your application’s components are spread across multiple zones within a single region (like North America, Europe, etc.).
- Simple Example: A load-balanced web tier spread across three zones within “us-central1”, with a database replicated across those same zones.
- Pros: Protects against single-zone outages, better for larger workloads.
- Cons: Slightly more complex to set up.
- Multi-Regional App Deployment
-
- What it is: Your application has major components running in multiple regions.
- Simple Example: The previous web app example, but also running in Europe. Traffic is routed to the closest region.
- Pros: Can withstand an entire region going offline, lower latency for global users.
- Cons: More costly and complex to manage data synchronization across regions.
- Global App Deployment
-
- What it is: Combines multiple regions and a global load balancer for maximum availability and performance.
- Simple Example: An e-commerce site with application servers worldwide, and a global database solution ensuring data consistency.
- Pros: Best for applications that need to be “always on” and very fast no matter where the user is.
- Cons: The most expensive and complex archetype to implement.
- Hybrid/Multi-Cloud App Deployment
-
- What it is: Deploys parts of your application in GCP and other parts on-premises or in another cloud provider.
- Simple Example: A website running on GCP but connecting to a legacy database that must remain in your company’s data center.
- Pros: Flexibility for when you can’t move everything to the cloud right away.
- Cons: Can be very complex, security needs careful planning across your whole environment.
Simple Examples
- Zonal: Basic website with a database in a single zone.
- Regional: Load-balanced website across multiple zones within a region.
- Multi-Regional: The same website replicated across North America and Europe.
- Global: E-commerce site with servers worldwide and a global database solution.
- Hybrid: Website on GCP connecting to a legacy database in your on-premises data center.
Important Note: Application architecture is complex, and there are other factors to consider beyond deployment archetypes.
9. Building Your GCP Landing Zone: Choosing the Right Approach
There are several ways to implement your Google Cloud Landing Zone design. The best approach depends on factors such as LZ complexity, your team’s expertise, and automation needs. Here’s a breakdown of common options:
Manual Configuration (GCP Console)
- What it is: Creating your LZ by clicking through the graphical interface of the Google Cloud console. You configure networks, set IAM permissions, create projects, etc. directly in your browser.
- Process: Utilize the GCP Console to manually create resources like folders, projects, VPC networks, and IAM policies.
- Pros: Good for very small LZs, or initially exploring Google Cloud’s features. No extra tooling to learn.
- Cons: Prone to errors if your LZ is complex. Difficult to replicate your setup across multiple environments. Changes are harder to track and revert.
Infrastructure as Code (IaC)
- What it is: Expressing your LZ’s desired configuration (network, IAM roles, etc.) as code or configuration files. Tools like Terraform and Cloud Deployment Manager then handle the actual resource creation on Google Cloud.
- Process: Define your landing zone infrastructure as code using tools like Terraform. This allows for version control, easy replication, and consistent configuration across environments.
Read: Cloud Deployments basics and fundamentals
- Pros: Promotes consistency – the exact same LZ can be deployed repeatedly. Changes are easily tracked (think version control). Often considered the best practice for larger or more complex LZs.
- Cons: Requires learning the syntax of the chosen IaC tool.
Google Cloud Deployment Manager
- What it is: Google-specific IaC tool using YAML-based templates to define resources and configurations.
- Process: Utilize declarative templates within Cloud Deployment Manager to define your landing zone resources and policies.
- Pros: Natively integrated with Google Cloud. Can combine infrastructure AND policy definitions within your templates.
- Cons: Less widely adopted than Terraform, so the learning curve might be steeper, depending on your team’s experience.
Marketplace Solutions
- What it is: Pre-configured LZ templates or solutions available directly within the Google Cloud Marketplace. These speed up implementation.
- Process: Leverage pre-built and validated landing zone solutions from the Google Cloud Marketplace. These solutions can be quickly deployed and customized to fit specific needs.
- Pros: Great if you need a basic LZ fast, or want a starting point to customize. Some solutions cater to specific compliance needs.
- Cons: May lack flexibility if you have very unique LZ requirements. Always review the Marketplace solution carefully to ensure it fits your needs.
Factors for Choosing an Approach
- LZ Complexity: How many resources, policies, and their dependencies?
- Team Expertise: Comfort with IaC tools, scripting, automation?
- Consistency Needs: How crucial is it to replicate your LZ across environments?
- Speed vs. Control: Do you need a LZ up and running quickly, or is fine-grained control your top priority?
Important Note: These approaches can be combined! You might start with the console for exploration, then transition to IaC, or customize a Marketplace solution with additional code-based configurations.
10. Best Practices for designing a Secure and Scalable GCP Landing Zone
A well-designed Google Cloud Landing Zone lays the groundwork for your cloud success. Follow these best practices to create a secure, scalable, and cost-effective foundation on GCP:
1. Planning and Requirements
- Define Clear Goals: Outline what your LZ should accomplish (support specific workloads, meet security mandates, etc.)
- Gather Requirements: Involve stakeholders across your organization (IT, security, developers) to understand their needs.
- Align with Business Objectives: Ensure your LZ design supports your overall business goals, not just immediate technical requirements.
2. Design and Implementation
- Start Small, Iterate: Begin with a foundational LZ for your initial workload, then expand and adapt as needs arise.
- Leverage Reference Architectures: Google provides recommended LZ blueprints ([link to Google’s LZ architectures]). Customize these to fit your requirements.
- Security from the Ground Up: Embed security into the design of your LZ from the start.
- Adopt IaC: Use Infrastructure as Code (Terraform, Cloud Deployment Manager) for consistency, change tracking, and automation.
- Modular Design: Design LZ components (network, IAM, etc.) as self-contained modules for easier updates and management.
3. Operations and Governance
- Centralize Monitoring and Logging: Use Cloud Monitoring and Cloud Logging to track LZ health and activity. Set up alerts for critical issues.
- Enforce Policies: Utilize Resource Manager and IAM to ensure consistent settings and prevent security vulnerabilities.
- Proactive Cost Management: Implement tagging, budgets, and right-sizing recommendations to optimize your spending.
4. Continuous Improvement
- Regular Reviews: Assess your LZ periodically to ensure it aligns with evolving needs or new Google Cloud services.
- Stay Updated on Best Practices: Google Cloud evolves rapidly. Staying current on new features and recommendations helps you maintain an optimized LZ.
- Feedback Loop: Collect feedback from LZ users (developers, admins) to guide improvement efforts.
Read: How GenAI cloud services are modernizing application architectures ?
Important Note: There’s no one-size-fits-all Landing Zone. These best practices serve as a strong foundation, but always tailor your implementation carefully to your organization’s specific needs.
11. GCP Landing Zone Checklist
Here’s a checklist for establishing a strong foundation for your cloud workloads. Tailor this process and leverage Terraform files for advanced workflows:
The Setup Process: Your GCP Foundations
- Establish Your Organization: Create your top-level Google Cloud Organization, set up initial administrative users, and link your payment method.
- Design Your Initial Architecture: Choose a structure for folders and projects, assign permissions, configure your network, and set up logging.
- Deploy Your Settings: Google Cloud generates setup instructions. Deploy directly in the browser or download files for customization.
- Apply Security and Support: Implement monitoring, security controls, and configure any necessary support services from Google Cloud.
1. Establish your organization, administrators, and billing
- Organization: Create the top-level container for all your Google Cloud resources.
- Users and groups: Define individual users and groups for managing access permissions.
- Administrative access: Assign roles granting varying levels of control over your GCP environment.
- Billing: Link a payment method to cover the costs of your Google Cloud resources.
2. Create an initial architecture
- Hierarchy and access: Organize resources in projects and folders, controlling access with permissions.
- Networking: Design your virtual private network (VPC) and subnets to structure communication.
- Centralize logging: Designate a central location for storing and analyzing logs from GCP services.
3. Deploy your settings
- Deploy or download: Choose to deploy your configuration directly or download files for customization.
4. Apply security and support settings
- Monitoring: Set up tools to continuously watch for security threats or configuration issues.
- Security: Implement controls like encryption, access restrictions, and data protection measures.
- Support: Choose the level of support you need from Google Cloud personnel.
12. Summary & Conclusion
A Google Cloud Landing Zone (LZ) provides a secure, scalable, and well-structured foundation for cloud deployments. Designing a successful LZ requires careful consideration of several key elements:
- Identity and Access Management (IAM): Securely controls who can access resources and what actions they’re authorized to perform.
- Resource Hierarchy: Logical organization of projects, folders, and the GCP Organization node determines how policies are applied and how costs are tracked.
- Network: VPCs, subnets, and firewall rules are essential for secure connectivity within GCP and with external environments (on-premises or other clouds).
- Security: Defense-in-depth strategies, encryption, monitoring, and access controls are crucial to protect sensitive data and workloads.
- Application Deployment Archetypes: Zonal, regional, multi-regional, global, and hybrid/multi-cloud models address varying needs for availability, latency, and cost.
- Implementation Approaches: Manual configuration (GCP Console), Infrastructure as Code (IaC), Cloud Deployment Manager, and Marketplace solutions offer different levels of automation and control.
- Best Practices: Planning, iteration, security by design, modularity, cost management, and continuous improvement are key for long-term LZ success.
- GCP Landing Zone Checklist: A step-by-step guide helps ensure a solid foundation for cloud deployments.
Conclusion
Building a well-designed Google Cloud Landing Zone is an investment that pays dividends. It unlocks the full potential of GCP, enabling secure cloud adoption, operational efficiency, and the ability to meet evolving business needs. By following the guidance and best practices outlined in this blog post, Cloud Architect’s can create Landing Zones that accelerate innovation, manage costs effectively, and strengthen their overall cloud security posture.
Remember: Your ideal Landing Zone is unique. Leverage the resources and tools provided by Google Cloud, and consider consulting with a GCP Architect to design and implement a solution tailored to your specific requirements.