Migrating to the cloud can be exciting, but as the organization grows within AWS landscape, managing all those resources can quickly become overwhelming. With a vast array of services and configuration options at your fingertips, it’s easy to end up with a sprawl of accounts that lack consistency, making it difficult to enforce security policies, track costs, and ensure compliance. This is where AWS Landing Zone come in. Imagine them as a pre-configured roadmap for your cloud journey. They provide a secure and organized foundation for deploying your workloads in AWS, bringing order to your cloud environment and streamlining your overall cloud experience.
An AWS Landing Zone is a multi-account AWS environment that follows best practices to provide a solid starting point for your cloud journey. It encompasses elements like account organization, network design, security safeguards, and centralized logging. In this blog post, we’ll be diving deep into the world of AWS Landing Zone architecture. We’ll explore what they are, the key benefits they offer, and the two main approaches to setting one up for your organization. We will finalize with the sample checklist which you can use it as a reference for building AWS Landing zone architecture.
1. Introduction to AWS Landing Zone
An AWS Landing Zone is a multi-account AWS environment meticulously crafted to follow best practices and provide a solid foundation for your cloud applications. It acts as a secure and organized starting point, eliminating the need to build your environment from scratch and navigate the complexities of AWS on your own. Think of it as a pre-configured city built with well-defined districts (accounts) for different purposes, secure traffic flow (network design), robust security measures (safeguards), and a central monitoring center (logging). This structured approach ensures:
- Isolation and Control: By separating resources into distinct accounts, you can isolate workloads and limit the blast radius in case of an incident. This also simplifies access control and strengthens your overall security posture.
- Scalability and Flexibility: The multi-account architecture allows you to easily scale your environment up or down as your needs evolve. Landing Zones provide the flexibility to create new accounts for specific purposes, ensuring your cloud infrastructure can grow alongside your organization.
- Standardized Governance: Landing Zones establish a consistent framework for managing your cloud environment. This includes pre-defined policies for security, compliance, and resource management, saving you time and effort while ensuring adherence to best practices.
- Centralized Logging and Monitoring: Having a central location for logging and monitoring all activity across your accounts provides greater visibility and simplifies troubleshooting. This allows you to identify potential issues early on and maintain optimal performance within your cloud environment.
Benefits of AWS Landing Zone
In essence, an AWS Landing Zone is more than just a multi-account setup; it’s a comprehensive framework designed to streamline your cloud experience, enhance security, and empower you to focus on what matters most: building and deploying innovative applications. But what exactly makes them so important and beneficial? Let’s explore the key advantages of implementing a Landing Zone:
Read: Complete guide on Cloud Landing Zones
- Standardized Account Structure: Landing Zones enforce a consistent way to organize your accounts. This eliminates sprawl and simplifies management by ensuring everyone knows where resources are located and how permissions are structured.
- Streamlined Governance: Pre-defined security policies and compliance standards are built into Landing Zones. This saves you time and effort compared to setting up these controls from scratch for each account, promoting a well-governed cloud environment.
- Enhanced Security: Landing Zones establish a baseline for secure configurations across all accounts. This reduces the risk of accidental misconfigurations and helps maintain a robust security posture throughout your AWS infrastructure.
- Cost Optimization: Landing Zones help you avoid resource sprawl and optimize cloud spending. By organizing resources logically, you can identify and potentially eliminate unnecessary services or instances, leading to more cost-effective cloud utilization.
- Faster Deployment: Think of a Landing Zone as a pre-built foundation, ready for use with pre-configured settings. This allows you to deploy workloads quicker compared to starting from scratch each time, accelerating your development and deployment cycles.
- Improved Operational Efficiency: Landing Zones centralize logging and monitoring, providing greater visibility into your entire AWS environment. This simplifies troubleshooting, streamlines resource management, and promotes operational efficiency.
- Scalability and Flexibility: The multi-account architecture inherent in Landing Zones allows for easy scaling. As your needs grow, you can create new dedicated accounts for specific purposes, ensuring your cloud infrastructure can adapt and evolve alongside your organization.
- Reduced Risk of Errors: By establishing pre-defined configurations and automated processes, Landing Zones minimize the potential for human error during account creation and configuration. This leads to a more reliable and secure cloud environment.
These benefits allow you to focus on what matters most: building and deploying innovative applications that drive your business forward.
2. Single AWS Account vs. Multi-AWS Account Strategy
As you venture into the vast landscape of AWS, a crucial decision arises: single account or multi-account strategy? Both approaches have their merits, and the optimal choice depends on your specific needs and cloud maturity. Let’s delve into the pros and cons of each strategy to guide you towards the best fit for your organization.
Read: 8 key design principles to build robust cloud architectures
1. Single Account: Simplicity with Limitations
A single account offers a straightforward setup, perfect for small-scale deployments or organizations new to AWS. Management is seemingly simpler, with all resources consolidated in one place. However, this simplicity comes at a cost:
- Security Concerns: A single point of failure. A security breach in this account exposes your entire AWS environment.
- Inconsistent Security: Implementing different security controls for diverse applications becomes challenging with a single account.
- Limited Scalability: As your workload grows, managing everything within a single account becomes cumbersome and hinders scalability.
- Compliance Challenges: Isolating data for regulatory compliance (e.g., PCI, GDPR) can be difficult with a single account structure.
2. Multi-Account: Security, Scalability, and Control
A multi-account strategy offers a more robust and secure foundation for your AWS environment. It involves creating dedicated accounts for different purposes (development, testing, production, etc.), workloads, or teams. Here’s why this approach is often preferred:
- Enhanced Security: Isolate resources and workloads. A breach in one account has minimal impact on others, significantly improving overall security posture.
- Granular Security Controls: Tailor security policies to specific application needs. This flexibility allows for stricter controls where necessary, like PCI compliance.
- Improved Scalability: Easily scale your cloud infrastructure by adding new accounts as your needs evolve. Each account can manage its own resources efficiently.
- Simplified Management: Organize resources logically across accounts for better visibility and easier management.
- Team Efficiency: Assign dedicated accounts to teams, preventing resource conflicts and fostering ownership.
- Clear Cost Allocation: Track costs associated with specific teams or projects by leveraging separate accounts for billing purposes.
- Compliance Advantages: Isolate sensitive data stores for easier compliance with data privacy regulations (e.g., GDPR).
3. Choosing the Right Path
- Single Account: Ideal for small-scale, non-critical workloads or organizations starting their AWS journey.
- Multi-Account: Recommended for growing environments, security-sensitive applications, or organizations with complex compliance requirements.
Remember, a multi-account strategy offers a more secure and scalable foundation for your AWS environment. However, it requires additional planning and management overhead. Consider your specific needs and weigh the advantages and limitations of each approach before making your decision.
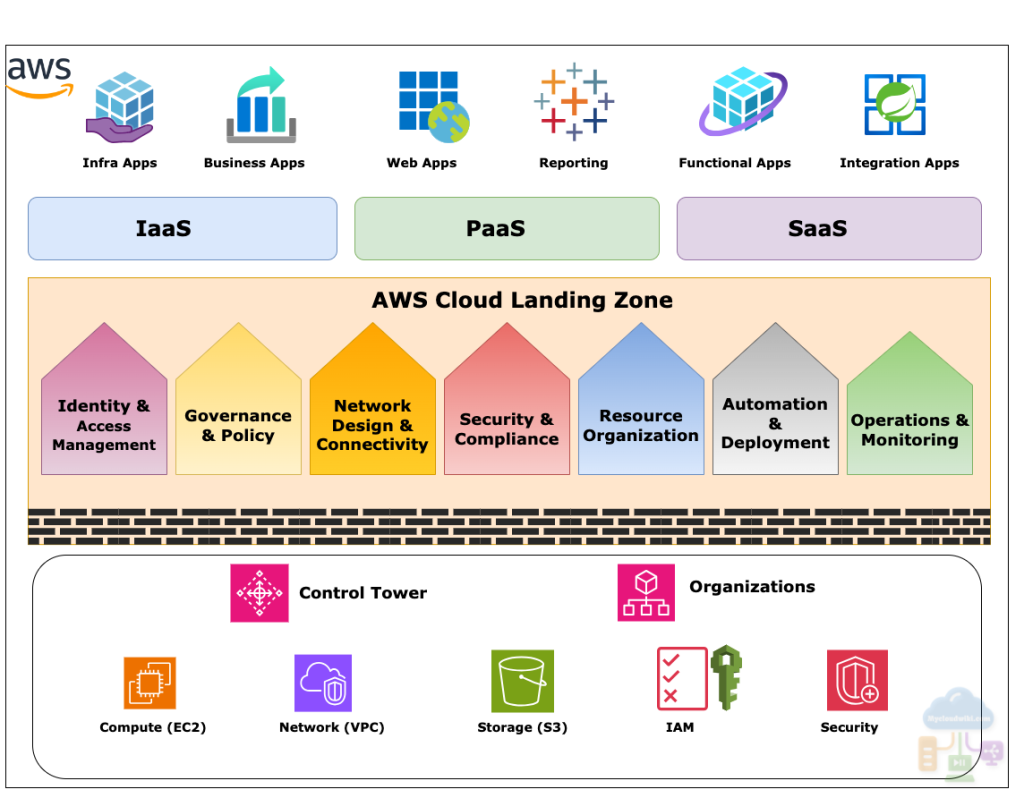
3. Key Components of an AWS Landing Zone Architecture
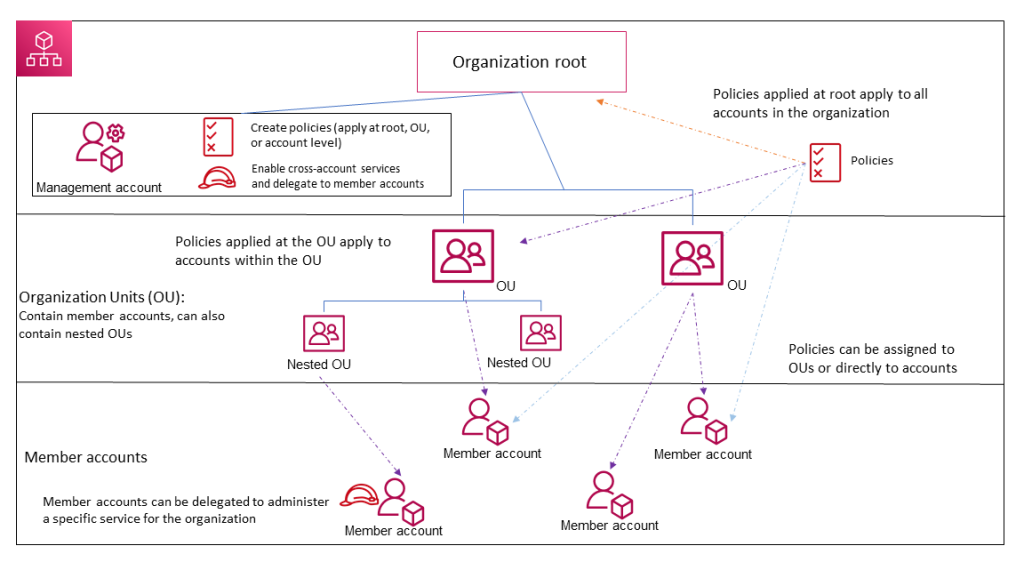
An AWS Landing Zone provides a secure, scalable, and well-structured multi-account environment within AWS. Its key elements include a strategic account organization (using Organizational Units), robust identity and access management (IAM), a carefully designed network architecture, strong security controls, and centralized logging and monitoring. A landing zone serves as a well-architected foundation, promoting operational efficiency, consistent governance, and simplified onboarding of new applications and workloads within your cloud environment. Let’s delve deeper into the key elements that make up an AWS Landing Zone and explore how they work together to create a secure and organized starting point for your cloud journey.
Read: High Availability vs Fault Tolerance vs Disaster Recovery
1. Account Structure
- Organizational Units (OUs): OUs are the primary way to group and logically organize multiple AWS accounts. Benefits include:
- Policy inheritance: Security and configuration controls applied at the OU level cascade down to member accounts.
- Simplified management: Apply actions and policies in bulk to a collection of accounts.
- Recommendations:
- Environments: Create OUs like “Development”, “Testing” and “Production” to isolate resources based on their stage in the development lifecycle.
- Functions: Establish OUs like “Shared Services” (for resources used across the organization) and “Security” (for centralized security tools and audit logs).
2. Identity and Access Management (IAM)
- Least Privilege: This principle means granting only the minimum permissions needed to perform a task. It minimizes security risks from overprivileged accounts.
- Role-Based Access Control (RBAC): Define IAM roles based on job functions (Developer, Administrator, etc.) and assign permissions to those roles rather than individual users. This simplifies management and ensures consistency.
- Federated Identity: Integrate with existing identity providers (like Active Directory or a third-party SSO service). This provides seamless login and eliminates the need to manage separate sets of credentials for AWS.
3. Network Design
- VPC Architecture: Virtual Private Clouds (VPCs) are the foundational network isolation construct. Plan for sufficient IP space and potential future expansion.
- Subnet Segmentation: Divide VPCs into subnets based on function (e.g., web tier, application tier, database tier) and security needs. This enhances network security and enables fine-grained traffic control.
- Peering and Connectivity:
- VPC Peering allows communication between VPCs within the same region.
- AWS Transit Gateway simplifies the connection of multiple VPCs and on-premises networks.
- Consider Direct Connect for dedicated, low-latency connectivity to your own data centers.
4. Security
- Security Groups and Network ACLs: Act as virtual firewalls – security groups at instance-level, network ACLs at subnet-level. Carefully design rules to balance security with necessary access.
- AWS Config: Tracks configuration changes and allows you to define rules to enforce compliance with best practices.
- GuardDuty: Uses machine learning to detect threats and anomalies.
- Security Hub: Centralizes alerts and provides a single view of your security posture across accounts.
5. Logging and Monitoring
- CloudTrail: Records all API calls for auditing and analysis. Enable across ALL accounts and send logs to a centralized log archive account for security and longevity.
- CloudWatch: Collects metrics, logs, and sets alarms for monitoring performance and availability. Use custom metrics for application-specific insights.
- Centralized Logging: Aggregate logs from all accounts to enable correlation, troubleshooting, and security analysis. Consider tools like Amazon S3, Elasticsearch, or third-party solutions.
4. Beyond the Basics: Advanced Considerations for Your AWS Landing Zone Architecture
While the core components of an AWS Landing Zone provide a solid foundation, there are additional considerations for advanced users seeking to optimize their architecture for specific needs. Here are some key areas to explore:
- Multi-Region Landing Zones: For geographically distributed deployments or disaster recovery needs, consider a multi-region Landing Zone architecture. This involves replicating the Landing Zone structure across multiple AWS Regions, ensuring redundancy and improved availability.
- Advanced Networking Design: Beyond basic segmentation, consider advanced network architectures like zero-trust security models or network access controls (NAC) for stricter access management.
- Data Residency and Encryption: For workloads with stringent data residency requirements, explore leveraging AWS services like AWS Outposts or Local Zones to keep data within specific geographic locations. Additionally, implement robust encryption strategies for data at rest and in transit.
- Cost Optimization and Budgeting: Utilize advanced cost management tools like AWS Cost Explorer and Budgets to delve deeper into resource utilization and identify potential savings opportunities. Consider implementing granular cost allocation by tagging resources and leveraging AWS Cost Allocation Tags.
- Continuous Integration and Delivery (CI/CD) Integration: Integrate your CI/CD pipeline with Landing Zone automation tools to automate infrastructure provisioning and configuration as part of your application deployment process. This streamlines deployments and promotes a DevOps approach.
- Security Automation and Orchestration: Implement tools like AWS Security Hub and Config Rules to automate security best practices checks and remediation actions across all accounts within your Landing Zone. This strengthens your overall security posture.
- Disaster Recovery and High Availability: Develop a comprehensive disaster recovery plan that integrates with your Landing Zone architecture. Consider features like AWS CloudTrail replication across regions for disaster recovery purposes.
5. Choosing right Landing Zone Approach
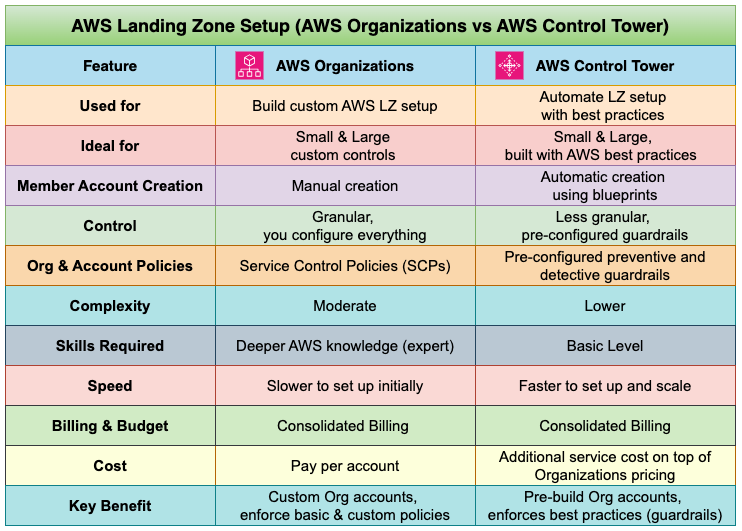
Now that you understand the benefits and key components of an AWS Landing Zone, it’s time to decide on the best approach for setting up AWS Landing Zone. There are two primary ways to implement an AWS Landing Zone, and the best choice for you depends on your organization’s needs, resources, and existing AWS expertise:
1. AWS Control Tower
- Managed Service: AWS Control Tower provides the easiest way to set up and govern a secure, multi-account environment. It automates the creation of accounts, implements security guardrails, and provides ongoing monitoring and governance.
- Advantages:
- Speed and Simplicity: Get started quickly with a well-architected foundation.
- Best Practices: Incorporates AWS security and governance recommendations seamlessly.
- Centralized Management: Manage your accounts and resources from a single console.
- Ideal for: Most organizations will benefit from the convenience and scalability offered by AWS Control Tower, especially if in-house AWS expertise is limited.
2. Custom-Built Landing Zone
- Full Customization: Design a landing zone from the ground up to align perfectly with your unique requirements.
- Flexibility: Choose specific services and configurations that meet your needs.
- Considerations:
- AWS Expertise Required: Building a custom landing zone demands deeper AWS knowledge and experience with services like IAM, networking, and security.
- Greater Responsibility: You’ll be responsible for implementing and maintaining all components and best practices.
- Ideal for: Organizations with strong AWS expertise, very specific or complex requirements, and the need for complete control over their cloud environment.
3. Choosing the Right approach:
For most users, AWS Control Tower offers a compelling solution. It provides a user-friendly, automated approach with built-in expertise, making it ideal for organizations seeking a quick and efficient way to establish a secure and well-governed AWS environment.
However, if you have advanced AWS expertise, complex existing infrastructure, or very specific requirements, a custom-built Landing Zone might be a better fit. It allows for complete control and customization to cater to your unique needs.
Ultimately, the best approach depends on your specific requirements, resources, and AWS experience. Consider your organization’s needs and comfort level with AWS to make the right decision for your Landing Zone implementation.
6. AWS Control Tower Overview
AWS Control Tower is a managed service designed to simplify and automate the provisioning and management of your AWS landing zone. It acts as a one-stop shop, offering a standardized approach to setting up the core infrastructure for your multi-account environment. AWS recommends that new customers begin their landing zone journey with AWS Control Tower. Its user-friendly interface and pre-configured settings simplify initial implementation.
1.AWS Control Tower: Key Features and Benefits
- Automated Multi-Account Setup: Control Tower orchestrates the provisioning of new AWS accounts, pre-configured with best practices for security and governance. This minimizes manual setup and reduces the chances of configuration errors.
- Built-In Guardrails: AWS Control Tower enforces preventive and detective guardrails across all your accounts. These customizable rules help ensure ongoing compliance with your organizational policies, flagging potential deviations from established best practices.
- Simplified Governance: Control Tower provides a central dashboard for monitoring account activity, resource deployment, and overall cloud environment health. This enhances visibility and empowers centralized governance.
- Integration with AWS Services: Control Tower seamlessly integrates with core AWS services like AWS Organizations, AWS Config, CloudTrail, and IAM for a unified and consistent approach to management and control.
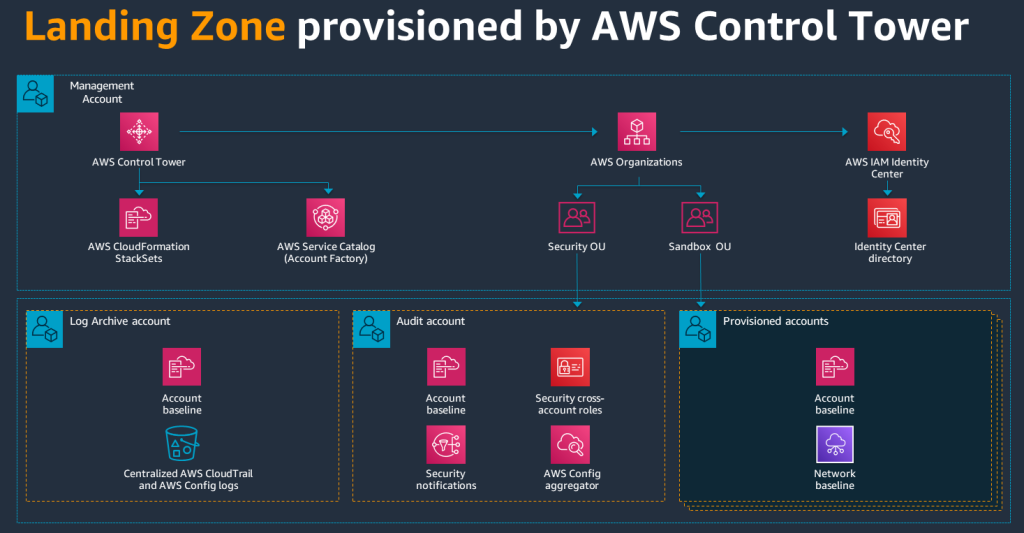
AWS Control Tower Structure and Functionality
AWS Control Tower simplifies the creation and management of a secure, multi-account AWS Landing Zone. Here’s a breakdown of its structure, account types, management account actions, and control mechanisms:
2. Control Tower Structure:
Control Tower creates a well-defined hierarchical structure within your AWS Organization. This structure consists of three main elements:
- Management Account: This is the root account in your Organization and the only account with direct access to Control Tower. It’s used for administering the Landing Zone and configuring Control Tower settings.
- Organizational Units (OUs): OUs act as logical groupings for your member accounts. You can create OUs based on purpose (development, testing, production), team ownership, or any other relevant category. This organization simplifies access control and resource management.
- Member Accounts: These are the accounts where you deploy your workloads and applications. Control Tower provisions and configures these accounts based on your chosen Landing Zone configuration and enforces pre-defined security policies.
3. Account Types Created by Control Tower:
Control Tower automatically creates several shared accounts to manage core Landing Zone functionalities:
- Logging Account: This account stores logs from all member accounts within your Landing Zone, providing centralized visibility for auditing and troubleshooting purposes.
- Audit Account: This account is used for security auditing purposes. It has access to CloudTrail logs from all member accounts to facilitate security compliance checks.
- Security Account: (Optional) This account can be used for additional security services like AWS Security Hub or AWS Config, further enhancing the overall security posture of your Landing Zone.
4. Actions Performed in the Management Account:
The Management Account is the central hub for interacting with Control Tower. Here are some key actions performed within this account:
- Configuring Control Tower: Define the Landing Zone configuration, including the selection of AWS Regions, creation of OUs, and configuration of shared accounts.
- Managing Organizational Units: Create, edit, and delete OUs to organize your member accounts logically.
- Managing Landing Zone Settings: Configure additional settings like custom member accounts, log retention policies, and IAM roles for Control Tower.
- Launching the Landing Zone: Once configurations are finalized, initiate the Landing Zone creation process, which automates account provisioning and configuration.
- Exception for Management Account: The root user and administrators within the management account have unrestricted access to perform any actions within the Landing Zone, even if those actions would be denied by controls. This is essential for maintaining administrative control and preventing the management account from becoming locked out due to overly restrictive controls. However, all actions taken within the management account are still logged for accountability and auditing purposes.
5. Control Mechanisms:
Control Tower enforces consistent security and governance across your Landing Zone through the use of controls:
- Service Control Policies (SCPs): These policies attached to OUs restrict the services and actions that users within those OUs can perform. This ensures adherence to security best practices and prevents unauthorized resource creation.
- Guardrails: Control Tower offers pre-defined guardrails that enforce specific configurations for member accounts. These guardrails cover aspects like encryption, logging, and IAM settings, ensuring a secure baseline for all accounts within your Landing Zone.
- AWS Config Rules: Control Tower integrates with AWS Config Rules to enforce additional custom configurations specific to your organization’s needs. These rules can trigger automated remediation actions if any configuration drift occurs, maintaining compliance.
By leveraging Control Tower’s automated account creation, pre-defined controls, and OU-based enforcement, you can establish a secure and well-governed foundation for your AWS workloads, reducing complexity and ensuring adherence to best practices.
7. Steps to build a Landing Zone with AWS Control Tower (Recommended)
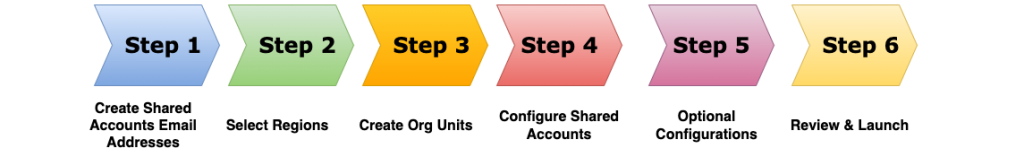
AWS Control Tower streamlines the Landing Zone creation process, making it an ideal choice for most users. Here’s a step-by-step walkthrough to get you started, highlighting the ease of use and built-in security features:
Step 1. Prepare Shared Account Email Addresses:
Control Tower utilizes shared accounts for critical Landing Zone functionalities like logging and auditing. The first step involves creating email addresses for these accounts. It’s important to remember that these addresses are for administrative purposes only and won’t be tied to individual users.
Step 2. Select Your Deployment Regions:
Specify the AWS Regions where you want to deploy your Landing Zone resources. This decision should consider factors like:
- Latency: Choose regions geographically close to your end-users for optimal performance.
- Data Residency: If you have regulations requiring data to remain within specific locations, select regions that comply with those requirements.
- Disaster Recovery: For disaster recovery purposes, consider deploying your Landing Zone across multiple regions to ensure redundancy and continued operations in case of disruptions.
Step 3. Organize with Organizational Units (OUs):
Control Tower empowers you to create Organizational Units (OUs) within your Landing Zone. These OUs act as logical groupings for your member accounts, promoting organization and simplifying access control. You can define OUs based on various criteria, such as development, testing, production environments, or specific teams within your organization.
Step 4. Configure Shared Accounts:
Control Tower automatically provisions a set of shared accounts that provide essential Landing Zone services. These include:
- Logging Account: This account centralizes logs from all member accounts within the Landing Zone, facilitating troubleshooting and security analysis.
- Audit Account: Control Tower uses this account to record all actions taken within the Landing Zone, ensuring a comprehensive audit trail for compliance purposes.
- Other Shared Services: Additional shared accounts might be created for functionalities like CloudTrail integration or organizational master keys.
Step 5. Optional Configurations:
While Control Tower offers a pre-configured Landing Zone based on best practices, it also allows for some customization:
- Custom Member Accounts: You can define blueprints for custom member accounts with specific configurations tailored to your needs. These custom accounts can then be easily provisioned within your Landing Zone.
- Log Retention: Control Tower allows you to define how long logs are retained within the logging account, enabling you to balance storage needs with compliance requirements.
Step 6. Review and Launch:
Once you’ve finalized your configuration choices, Control Tower provides a comprehensive review stage. This allows you to verify all your selections before launching. After a final confirmation, Control Tower takes over, automating the creation and configuration of your entire Landing Zone based on AWS best practices.
Benefits of Using AWS Control Tower:
- Effortless Setup: Control Tower’s user-friendly interface streamlines the Landing Zone creation process, making it accessible even for those with limited AWS experience.
- Reduced Errors: By automating the setup and configuration, Control Tower minimizes the potential for human error, ensuring a secure and reliable foundation for your cloud deployments.
- Pre-built Security: Control Tower enforces a set of pre-defined best practices for security, compliance, and account organization within your Landing Zone. This saves you time and ensures you’re adhering to industry standards from the outset.
- Faster Time-to-Value: The automation capabilities of Control Tower enable rapid Landing Zone deployment, allowing you to begin deploying your applications and workloads sooner.
- Reduced Management Overhead: Control Tower takes care of the ongoing maintenance of the core Landing Zone infrastructure. This frees up your team to focus on managing your workloads and applications, maximizing their efficiency.
8. AWS Organizations Overview
While AWS Control Tower offers a user-friendly solution for many, some organizations require the ultimate control and customization that comes with a custom Landing Zone built using AWS Organizations. This approach empowers you to tailor every aspect of your Landing Zone to meet your specific needs.
What is AWS Organizations?
AWS Organizations is a powerful service that helps you centrally manage and govern multiple AWS accounts within your organization. Enables you to create a hierarchical structure for your accounts (using Organizational Units – OUs), reflecting your business units, development environments (dev/test/prod), or security needs.
Key Terminology to remember
- Organization: The overarching umbrella for all your connected AWS accounts. This includes a special management account and all the other member accounts.
- Management Account: The “command center” of your organization. From here, you create new accounts, manage policies, and handle consolidated billing.
- Member Account: Individual AWS accounts that you invite into the organization. Once joined, they follow the rules (policies) you set from the management account.
- Organizational Unit (OU): Think of these as folders to group accounts logically. OUs can even contain other OUs, letting you build a hierarchy that matches your business.
- Root: The very top of your organization’s tree. This is created automatically for you.
- Service Control Policy (SCP): SCPs are like customizable fences. They control which AWS services and actions accounts are allowed to use.
Basic Organization Structure
- Root: The top-level container in AWS Organizations. It encompasses all accounts and OUs within your organization.
- Organizational Units (OUs): Create OUs to group accounts based on factors like security needs, environment (dev/test/prod), regulatory compliance, or business units.
- Accounts: AWS Organizations lets you create new member accounts or invite existing accounts into the organization.
Managing Policies with SCPs
- Service Control Policies (SCPs): Imagine SCPs as guardrails that define permitted services and actions for users within specific accounts or OUs. They ensure users only have access to what they need.
- Blacklist vs. Whitelist: SCPs can be configured in two ways:
- Deny List (Blacklist): Explicitly prevent access to specific services or actions.
- Allow List (Whitelist): Only allow access to specifically defined services or actions.
- Policy Inheritance: SCPs attached to an OU apply to all member accounts and nested OUs within it. SCPs directly attached to an account affect only that specific account.
- Blacklist vs. Whitelist: SCPs can be configured in two ways:
Consolidated Billing
- Simplified Payment: The management account receives a single bill that reflects the total usage costs across all member accounts in your organization. No more juggling multiple bills!
- Cost Allocation Tags: These custom tags act like labels you can attach to resources across accounts. They allow for granular cost tracking by associating them with departments, projects, or any other breakdown that helps you analyze your cloud spending effectively.
Additional Critical Concepts
- Enable All Features: Ensure this setting is activated to unlock the full potential of AWS Organizations, including access to certain policy types.
- Organization-Wide Backup Policies: Utilize AWS Backup to centrally define and deploy consistent backup strategies across all accounts within your organization.
- Delegated Administration (Advanced): For complex scenarios, grant a trusted account within your organization limited administrative privileges over a designated set of accounts and actions.
9. Steps to build a custom Landing Zone with AWS Organizations (Advanced)
AWS Organizations is a foundational service for effectively managing multiple AWS accounts. Understanding these concepts sets the stage for securing, governing, and optimizing costs within your cloud environment. Here’s a step-by-step guide to help you build a custom Landing Zone with AWS Organizations:
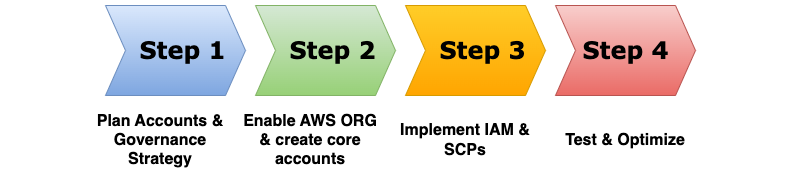
Step 1. Planning and Design:
-
Define Requirements:
- Conduct a thorough assessment of your organization’s security posture, compliance requirements, and workload types. This analysis will inform the structure and components you integrate into your Landing Zone.
- Consider factors like data sensitivity, regulatory requirements (e.g., HIPAA, PCI DSS), and disaster recovery strategies when defining your needs.
-
Account Structure and OUs:
- Design a logical and hierarchical account structure using OUs within your AWS Organization. This structure should group accounts based on purpose (development, testing, production), workload type (e.g., PCI compliant applications), or team ownership.
- Example: Create an OU named “Development” to house all development accounts. Within “Development,” you might create sub-OUs for specific development teams or projects.
- Design a logical and hierarchical account structure using OUs within your AWS Organization. This structure should group accounts based on purpose (development, testing, production), workload type (e.g., PCI compliant applications), or team ownership.
-
Governance Strategy:
- Develop a comprehensive governance strategy that outlines the security policies, access controls, and baselines you will enforce within your Landing Zone. This strategy should address areas like:
- Identity and Access Management (IAM): Define best practices for IAM roles, policies, and multi-factor authentication (MFA) requirements.
- Security Baselines: Specify the desired configuration state for core AWS services like S3, EC2, and IAM across all member accounts.
- Compliance: Outline any specific compliance requirements your organization needs to adhere to (e.g., data residency, encryption standards).
- Develop a comprehensive governance strategy that outlines the security policies, access controls, and baselines you will enforce within your Landing Zone. This strategy should address areas like:
Step 2. Implementation:
-
Enable AWS Organizations:
- Activate AWS Organizations within your management account. This establishes the central hub for managing all accounts within your Landing Zone. The management account should be highly secure and have limited access granted for administrative purposes only.
-
Create Core Accounts:
- Utilize AWS Organizations to create accounts dedicated to specific Landing Zone functionalities:
- Security Account: This account will house security tools and configurations for your Landing Zone. Deploy services like AWS Security Hub, Amazon GuardDuty, and AWS Config for centralized security management.
- Log Archive Account: Store logs from all member accounts within this dedicated account. Utilize Amazon S3 buckets with appropriate access controls (e.g., bucket policies) to ensure secure and long-term log storage.
- Shared Services Account: This account will host shared resources that multiple member accounts can leverage. Examples include AWS Key Management Service (KMS) for centralized encryption key management or AWS Secrets Manager for storing sensitive configuration data.
- Utilize AWS Organizations to create accounts dedicated to specific Landing Zone functionalities:
-
Establish Network Infrastructure:
- Create VPCs: Utilize AWS Organizations to manage VPC creation within member accounts. Ensure VPCs adhere to your defined security best practices and network segmentation requirements. Some considerations include:
- Logical Separation: Create separate VPCs for development, testing, and production environments to isolate traffic and workloads.
- Subnet Design: Within each VPC, define subnets that group related resources based on function or security requirements. For example, create public subnets for resources requiring internet access and private subnets for internal-facing resources. Utilize security groups within subnets to control inbound and outbound traffic flow.
- Create VPCs: Utilize AWS Organizations to manage VPC creation within member accounts. Ensure VPCs adhere to your defined security best practices and network segmentation requirements. Some considerations include:
Step 3. Security and Governance: Enforcing Controls and Maintaining Compliance
-
IAM Roles and Policies:
- Configure IAM roles and policies within member accounts to enforce granular access control based on the principle of least privilege. This ensures users only have the permissions they need to perform their specific tasks.
- IAM Roles: Create IAM roles that define specific sets of permissions for different user groups or applications within your Landing Zone. For example, create a role for developers with access to development environments and another role for operations teams with broader access for managing production resources.
- IAM Policies: Attach IAM policies to IAM roles or users to grant them access to specific resources or actions within your AWS environment. Utilize pre-defined AWS managed policies as a starting point and customize them as needed.
-
Service Control Policies (SCPs):
- Define SCPs at the OU level to restrict specific AWS service actions or enforce configurations across groups of accounts within your organization. This allows you to implement consistent security guardrails across your Landing Zone.
- Example: Create an SCP at the “Development” OU level that restricts users from creating Amazon S3 buckets with public access.
-
Centralized Logging and Monitoring:
- Implement a central logging solution to collect logs from all accounts within your Landing Zone. This allows for centralized analysis, troubleshooting, and security monitoring. Utilize services like:
- AWS CloudTrail: Tracks API calls made within your accounts, providing a record of user activity and resource configuration changes. Enable CloudTrail in all member accounts and configure it to deliver logs to the central log archive account.
- Amazon CloudWatch Logs: Centralizes log data from various AWS services and applications, enabling comprehensive log analysis and filtering. Forward logs from member accounts to a central CloudWatch Logs log group within the log archive account for aggregation and analysis.
- Configure monitoring tools like Amazon CloudWatch to collect metrics and monitor the health and performance of your resources within the Landing Zone. Establish dashboards for key metrics (CPU utilization, network traffic) to gain real-time visibility into your cloud environment.
- Implement a central logging solution to collect logs from all accounts within your Landing Zone. This allows for centralized analysis, troubleshooting, and security monitoring. Utilize services like:
-
Security Baselines:
- Define and enforce security baselines across member accounts using tools like AWS Config Rules. These baselines should include configurations for core AWS services like IAM, S3, EC2, and others relevant to your workloads.
- Example Baseline Rule: A Config Rule can ensure that MFA is enabled for the root user in all member accounts.
- Utilize AWS Config to continuously evaluate your member accounts against your defined baselines. Config can automatically trigger remediation actions if any configuration drift is detected, ensuring your Landing Zone adheres to your security best practices.
- Consider leveraging AWS Security Hub for centralized aggregation and analysis of security findings from various AWS services. This allows you to identify and prioritize potential security vulnerabilities within your Landing Zone.
- Define and enforce security baselines across member accounts using tools like AWS Config Rules. These baselines should include configurations for core AWS services like IAM, S3, EC2, and others relevant to your workloads.
Step 4. Ongoing Management: Maintaining a Secure and Optimized Landing Zone
-
-
-
Continuous Monitoring:
- Continuously monitor your Landing Zone for security vulnerabilities, configuration drift, and resource utilization. Utilize the centralized logging and monitoring tools you established to stay vigilant.
- Proactively address any security findings identified by AWS Security Hub or CloudTrail logs.
- Regularly review CloudWatch dashboards to identify potential performance bottlenecks or resource inefficiencies.
-
Policy Updates:
- Regularly review and update your security policies, governance controls, and IAM configurations as your cloud environment evolves. This ensures your Landing Zone remains secure and adapts to your changing needs.
- Stay informed about new AWS security best practices and incorporate them into your Landing Zone architecture as needed.
-
Resource Optimization:
- Monitor resource utilization within your member accounts to identify opportunities for cost optimization. AWS offers various tools like Amazon Cost Explorer and Amazon Trusted Advisor to help you identify underutilized resources or potential cost savings.
- Consider using AWS service quotas within SCPs to limit resource consumption and prevent unexpected costs.
-
-
Benefits of a Custom Landing Zone with AWS Organizations:
- Ultimate Control and Flexibility: AWS Organizations empowers you to tailor every aspect of your Landing Zone to meet your specific needs, unlike the pre-configured approach of AWS Control Tower.
- Granular Governance: Enforce security policies and access controls at the OU level with SCPs, enabling comprehensive governance across your organization.
- Scalability: The AWS Organizations framework scales effortlessly as your cloud footprint expands, allowing you to seamlessly add new accounts and manage them centrally.
Remember: Building and maintaining a custom Landing Zone requires significant expertise and ongoing management effort. However, with a well-defined plan, a robust architecture built on AWS Organizations, and a commitment to continuous improvement, you can create a secure, scalable, and cost-effective foundation for your AWS environment.
10. AWS Landing Zone Design Considerations and Best Practices
Regardless of whether you choose AWS Control Tower or a custom approach, establishing a secure and well-governed AWS Landing Zone requires careful planning and implementation. Here, we’ll explore key design considerations and best practices that apply to both approaches:
Read: Generative AI Basics and Fundamentals
1. Account Structure and Governance:
- Multi-account Strategy: Implement a multi-account strategy to segregate workloads and resources based on function (development, testing, production), environment (regional, global), or ownership (teams, departments). This promotes security isolation and simplifies access control.
- Organizational Units (OUs): Utilize OUs within AWS Organizations (or folders in Control Tower) to logically group accounts for better organization and management. Structure your OUs based on the criteria mentioned above for a clear and maintainable hierarchy.
- Identity and Access Management (IAM): Enforce the principle of least privilege with IAM. Configure roles and policies that grant users only the permissions they need to perform their specific tasks. Utilize multi-factor authentication (MFA) for an additional security layer.
- Governance Controls: Develop a comprehensive governance strategy that outlines security policies, access controls, and compliance requirements for your Landing Zone. Tools like AWS Config, Service Control Policies (SCPs), and AWS Security Hub can be leveraged to enforce these controls and maintain a secure environment.
2. Network Design and Security:
- Virtual Private Clouds (VPCs): Utilize VPCs to segment your workloads and resources within the Landing Zone. Create separate VPCs for development, testing, and production environments to isolate traffic and enhance security. Define subnets within VPCs to further group related resources based on function or security requirements.
- Security Groups: Implement security groups within your VPCs to control inbound and outbound traffic flow. Configure security groups with restrictive rules by default, allowing only authorized traffic.
- Network Access Control Lists (ACLs) (Optional): For an additional layer of security at the subnet level, consider using Network Access Control Lists (ACLs) to further restrict traffic flow within your VPCs.
- AWS Security Best Practices: Adhere to AWS security best practices for all services you utilize within your Landing Zone. This includes encryption of data at rest and in transit, strong password policies, and regular security audits.
3. Automation and Infrastructure as Code (IaC):
- Infrastructure as Code (IaC): Utilize IaC tools like AWS CloudFormation to define the infrastructure components of your Landing Zone as code. This ensures consistent configuration, simplifies deployment and updates, and minimizes human error.
- Automation Tools: Consider incorporating additional automation tools like AWS CodePipeline for continuous integration and continuous delivery (CI/CD) of your Landing Zone infrastructure. This enables automated deployment and management of your Landing Zone configuration.
4. Logging, Monitoring, and Cost Optimization:
- Centralized Logging: Implement a central logging solution like Amazon CloudTrail and Amazon CloudWatch Logs to collect and analyze logs from all accounts within your Landing Zone. This allows for centralized troubleshooting, security monitoring, and compliance audits.
- Monitoring: Configure monitoring tools like Amazon CloudWatch to collect metrics and monitor the health and performance of your resources within the Landing Zone. Establish dashboards for key metrics to gain real-time visibility into your cloud environment.
- Cost Optimization: Enable cost tracking with AWS Cost Explorer to identify potential cost savings opportunities. Utilize cost allocation tags to categorize resources and track spending by department, project, or any other relevant criteria. Explore options like Reserved Instances and Spot Instances for predictable workloads or fault-tolerant applications to optimize your cloud spending.
By following these design considerations and best practices, you can establish a robust foundation for your AWS Landing Zone, regardless of the deployment approach you choose. Remember, your Landing Zone is a dynamic environment that requires ongoing monitoring, security reviews, and adjustments to ensure it remains secure, scalable, and cost-effective in the face of evolving needs.
11. Additional Considerations for robust AWS Landing Zone Architecture
While the core design considerations focus on security, governance, and cost optimization within your AWS environment, a well-designed robust Landing Zone also needs to address how it integrates with your existing infrastructure and prepares for potential disruptions. Here’s a breakdown on key areas for further consideration:
1.Hybrid Cloud Integration
- Connectivity:
- Direct Connect: Offers dedicated, low-latency connectivity for production workloads requiring consistent network performance and high bandwidth. Plan carefully for physical links and routing.
- VPN: A cost-effective option for less demanding or temporary connectivity needs. Consider site-to-site VPN or client-based VPN depending on the nature of access needed.
- Security Considerations:
- Extend IAM: Federate identities where possible for consistent access control across on-premises and AWS. Carefully manage least-privilege principles.
- Network Segmentation: Implement firewalls and controls to protect sensitive workloads, both in the cloud and on-premises.
- Data Encryption: Ensure data is encrypted in transit and at rest, especially when traversing the public internet for hybrid connections.
- Monitoring: Establish unified monitoring solutions to gain visibility into both your AWS resources and on-premises infrastructure.
2. Disaster Recovery (DR)
- Backup Strategies:
- AWS Backup: Centralized backup management for services like EBS, RDS, DynamoDB, and more. Establish backup schedules and cross-region replication policies for robust data protection.
- Snapshots: Leverage snapshots for point-in-time recovery of EBS volumes and other services.
- Multi-Region Architectures:
- Active-Passive: Deploy a scaled-down version of your application in another AWS region. In a disaster, failover traffic to the secondary region.
- Active-Active: Distribute traffic across multiple regions normally, providing higher resilience and potential for lower latency to users.
- Pilot Light: Maintain a minimal footprint in a secondary region, ready to be scaled up rapidly in the event of a disruption.
Important Considerations
- Recovery Time Objective (RTO): How quickly must you recover systems? This drives DR strategy (active-active vs. backup and restore).
- Recovery Point Objective (RPO): How much data loss is acceptable? This dictates the frequency of backups and snapshots.
- Testing: Regularly test your DR plans; untested backups and failover procedures breed false confidence.
Read: Basic concepts of Cloud configurations and deployments
3. Integration with Existing Systems
- If you’re migrating from an existing data center or other cloud providers, carefully plan the integration between your legacy systems and your new AWS Landing Zone.
- Consider phasing migrations and hybrid connectivity solutions during the transition.
4. Account Vending Machine:
- Consider automating the process of creating and configuring new accounts using a tool like AWS Service Catalog. This can streamline onboarding and ensure consistency across accounts.
5. Multi-Region Cost Optimization:
- Factor in data transfer costs when choosing regions for your workloads, as this can affect your overall expenses.
- Explore services like CloudFront (AWS’s Content Delivery Network) to reduce data egress costs by caching content closer to users.
6. AWS Trusted Advisor:
- Leverage this service for recommendations on cost optimization, security improvements, performance, and fault tolerance within your Landing Zone.
7. Edge Services:
- If your applications serve a global user base, consider using CloudFront to improve performance and reduce latency.
- Route 53 (AWS’s DNS service) offers advanced routing policies such as geolocation and latency-based routing to optimize user experiences.
8. AWS Marketplace:
- Explore solutions in the AWS Marketplace that can simplify the deployment of pre-configured components for common use cases (security tools, monitoring solutions, etc.) within your Landing Zone.
9. DevOps Integration:
- Incorporate your Landing Zone into your CI/CD pipelines to streamline secure infrastructure provisioning alongside application deployment.
- Use tools like CloudFormation to manage infrastructure updates as code.
10. Security Incident Response:
- Have a well-defined incident response plan that extends into your AWS environment.
- Include clear communication procedures, roles, and escalation paths.
- Integrate security services like GuardDuty and Security Hub into your response workflows.
11. Compliance:
- Understand which regulatory frameworks (HIPAA, PCI-DSS, FedRAMP, GDPR, etc.) apply to your workloads.
- Tailor your Landing Zone design with appropriate controls for data handling, encryption, access restrictions, and audit logging to align with requirements.
12. Continuous Evolution:
- AWS constantly releases new services and updates. Review your Landing Zone regularly to determine if you can benefit from these innovations.
- Use the Well-Architected Framework to periodically evaluate your environment for ongoing enhancements.
12. AWS Landing Zone Setup Checklist
Building a well-structured AWS Landing Zone is key to streamlining cloud operations and maintaining a strong security posture. Use this checklist as your roadmap to establish the core elements needed for long-term success
1.Account Structure Planning
- Organizational Units (OUs): Map out potential OUs based on environments (dev/test/prod), business units, security tiers, etc.
- Core Accounts: Designate accounts for essential purposes (Security, Log Archive, Shared Services).
2.Security Baseline
- IAM Essentials: Enforce least privilege principles; create foundational roles (admin, developer, read-only).
- Activate Core Services: Enable CloudTrail (all regions), GuardDuty, consider Security Hub.
- Centralized Logging: Establish a log archive account and configure cross-account forwarding.
3.Governance
- SCPs (if custom build): Draft initial “deny” list SCPs to prevent critical misconfigurations (e.g., disabling CloudTrail).
- AWS Control Tower (if using): Review pre-configured guardrails and determine if customizations are needed.
4.Networking
- VPC Planning: Outline basic VPC needs (public/private subnets), IP addressing scheme (consider future growth).
- Connectivity: Note potential connectivity needs (Direct Connect for hybrid environments, Transit Gateway for multi-VPC scenarios).
5.Next Steps
- Refine and Expand: Tailor this checklist to your organization’s specific needs and security posture.
- Automation (IaC): Research tools (CloudFormation, Terraform) to manage your Landing Zone as code.
- Testing: Develop rigorous test plans before deploying changes to production environments.
Important Note: This is a simplified checklist. Building a comprehensive Landing Zone demands deeper AWS expertise and ongoing refinement.
13. Summary and Conclusion:
An AWS Landing Zone establishes a secure and scalable multi-account foundation for your cloud operations. Its core elements include strategic account organization (using Organizational Units), robust identity and access management (IAM), a well-designed network architecture, comprehensive security controls, and centralized logging and monitoring. Key benefits of a Landing Zone are enhanced security, simplified governance and compliance, improved operational efficiency, and the ability to scale for future needs. Organizations can choose between AWS Control Tower (a managed service for quick, best-practice deployments) or build a custom Landing Zone for maximum flexibility and control.
Conclusion
A well-designed AWS Landing Zone is crucial for organizations embracing cloud computing. By establishing this robust foundation, you streamline the provisioning of new workloads, strengthen security posture, and simplify compliance efforts. The investment in a Landing Zone pays dividends in long-term operational efficiency and enables you to confidently leverage the full potential of AWS services for your business.
Building a robust AWS Landing Zone is an ongoing journey! Let’s keep the conversation going:
- Share Your Experiences: Did you implement a Landing Zone? What challenges did you encounter, and what successes did you achieve? Please comment your insights which can be helpful to others.
- Ask Your Questions: Are there any specific areas of a Landing Zone design you’d like to explore further? Don’t hesitate to ask in comment section.
- Suggest Topics: Are there related areas of AWS architecture or cloud security that you’d like to see covered in future blog posts? Let us know!